New CloudFormation Templates - NAT Gateway, Static website, Security
We released four new CloudFormation templates. Using our Infrastructure as Code templates will help you to bootstrap common setups on Amazon Web Services (AWS) within minutes. Our templates are exclusively designed for AWS CloudFormation, the Infrastructure as Code services on AWS. Learn more about our Templates for AWS CloudFormation on GitHub.
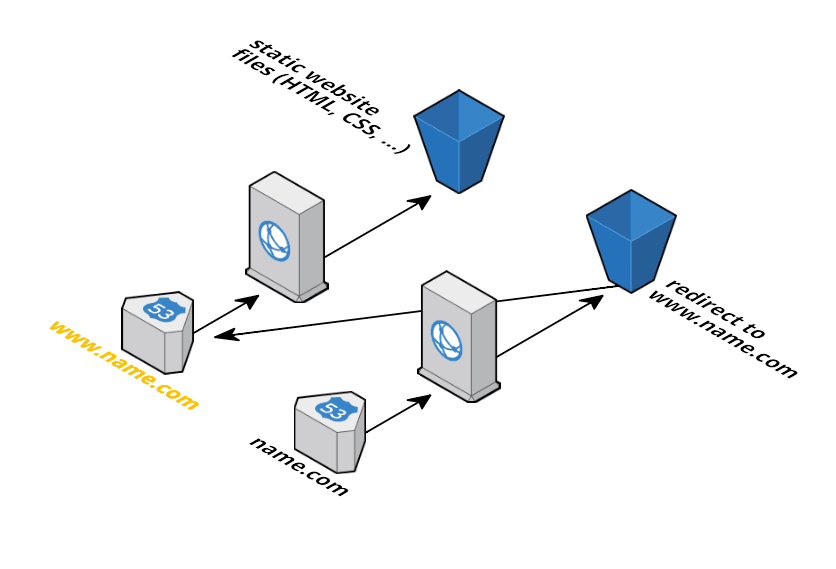
Static website
This template describes the infrastructure for hosting a static website behind a CDN.
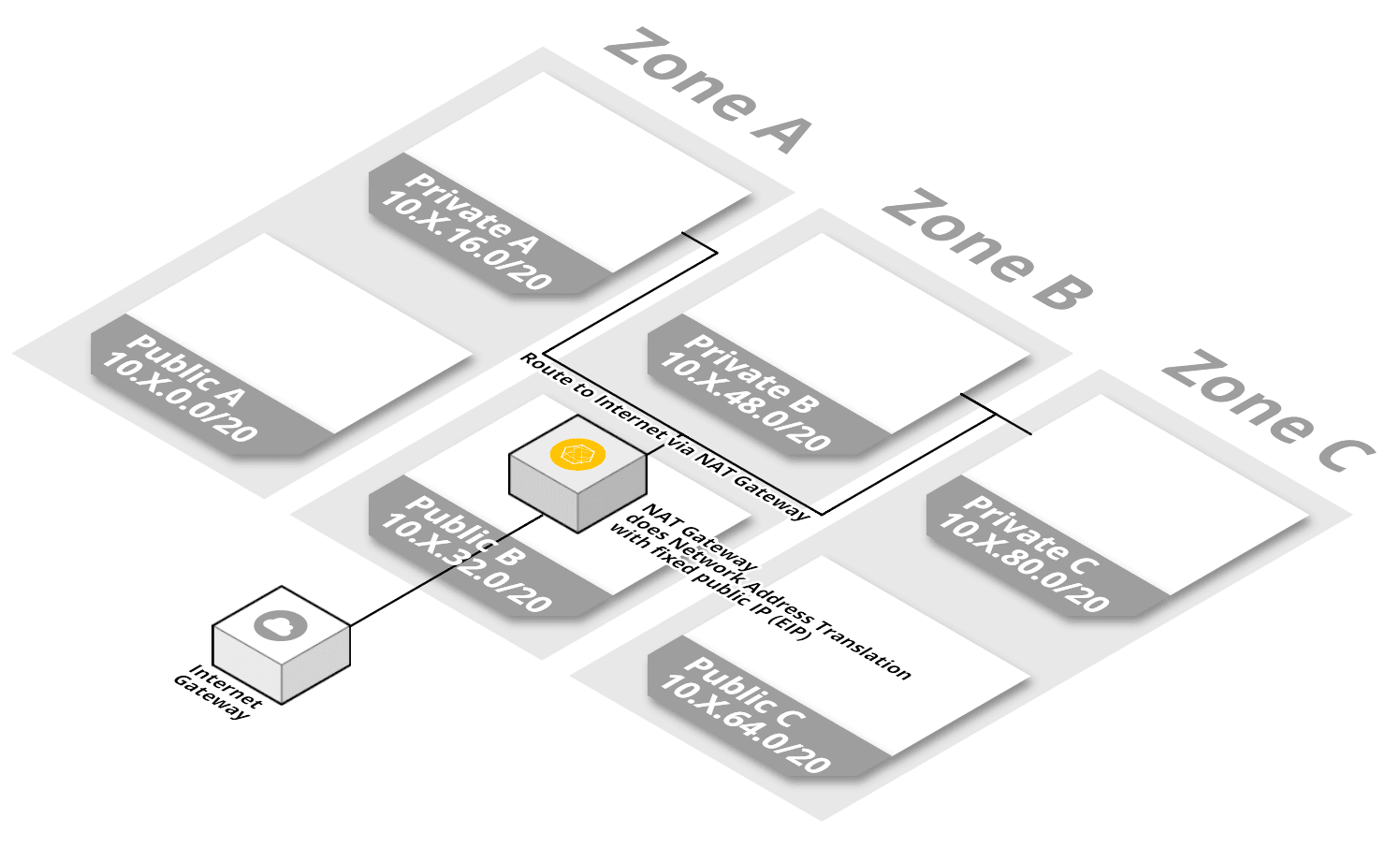
NAT Gateway
This template creates a NAT Gateway that forwards HTTP, HTTPS and NTP traffic from private subnets to the Internet.
Security
CloudTrail across all regions
This template enables CloudTrail to records AWS API calls across all regions in your AWS account. API calls are archived in S3 and also pushed CloudWatch Logs. If new API calls are available in S3 a SNS topic is notified.
Account Password Policy
This template creates an account password policy for your IAM users. You can:
- set IAM user passwords to be valid for only the specified number of days.
- prevent IAM users from reusing a specified number of previous passwords.
- specify the minimum number of characters allowed in an IAM user password.
- require that IAM user passwords contain at least one lowercase character from the ISO basic Latin alphabet (a to z).
- require that IAM user passwords contain at least one uppercase character from the ISO basic Latin alphabet (A to Z).
- require that IAM user passwords contain at least one numeric character (0 to 9).
- require that IAM user passwords contain at least one nonalphanumeric character.
- permit all IAM users in your account to use the IAM console to change their own passwords.
- prevent IAM users from choosing a new password after their current password has expired.
Or just use the suggested defaults.
Support
We offer support for our CloudFormation templates: setting up environments based on our templates, adopting templates to specific use cases, resolving issues in production environments. Hire us!
