New CloudFormation Templates - VPC bastion host, Jenkins, Security AWS Config
We released four new CloudFormation templates and updated the other templates to work together with the new SSH bastion host. Using our Infrastructure as Code templates will help you to bootstrap common setups on Amazon Web Services (AWS) within minutes. Our templates are exclusively designed for AWS CloudFormation, the Infrastructure as Code services on AWS. Learn more about our Templates for AWS CloudFormation on GitHub.
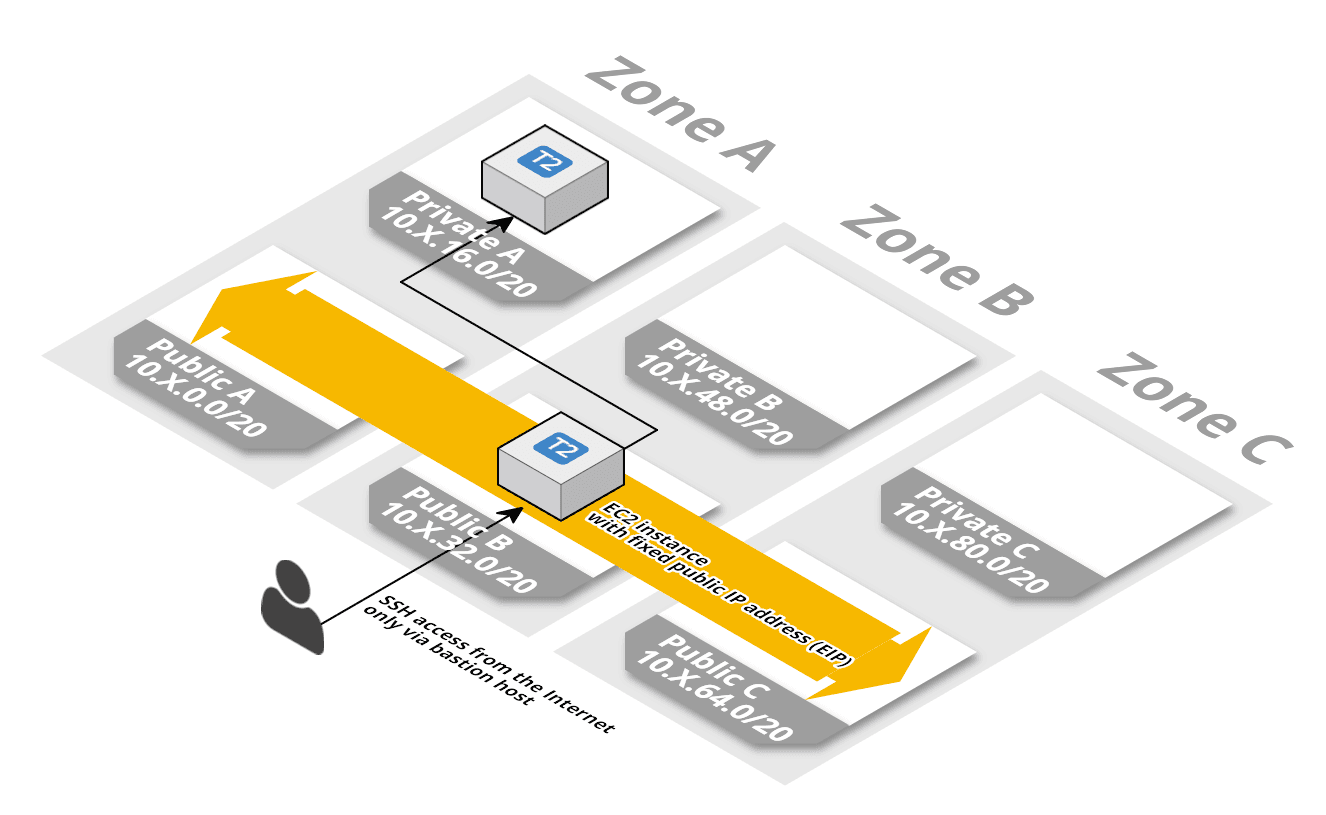
VPC: SSH bastion host/instance
This template describes a highly available SSH bastion host/instance. SSH Port 22 is open to the world. You can enable the default ec2-user access protected by the referenced EC2 KeyPair. You can also enable personalized SSH access by using the IAM users and their configured public keys. Use ssh -A user@ip to enable forwarding of the authentication agent connection when connection to the bastion host.
Jenkins
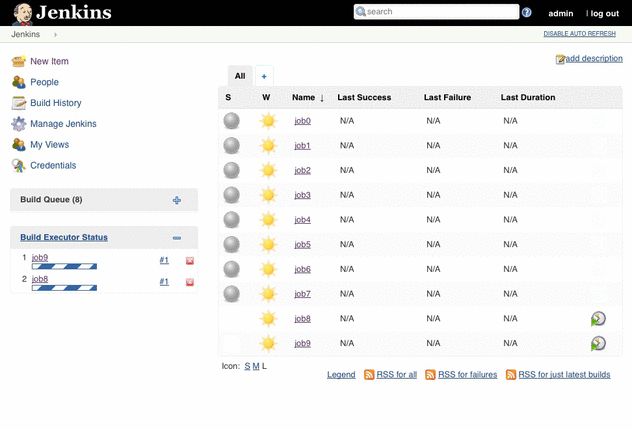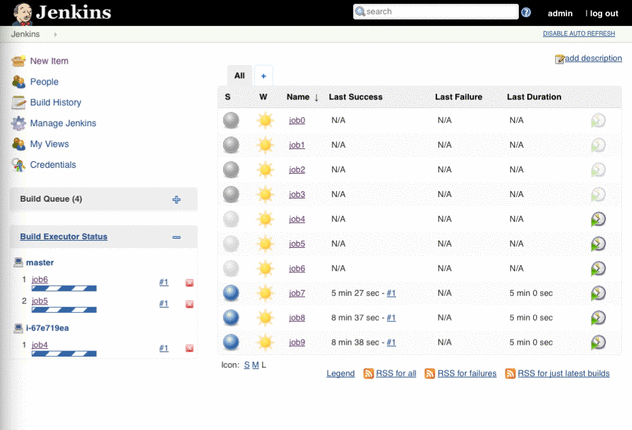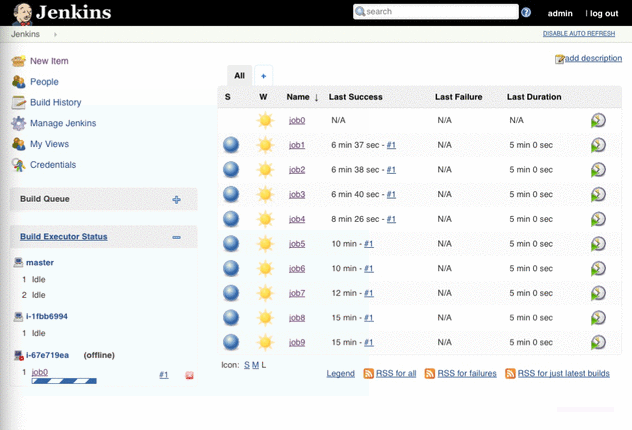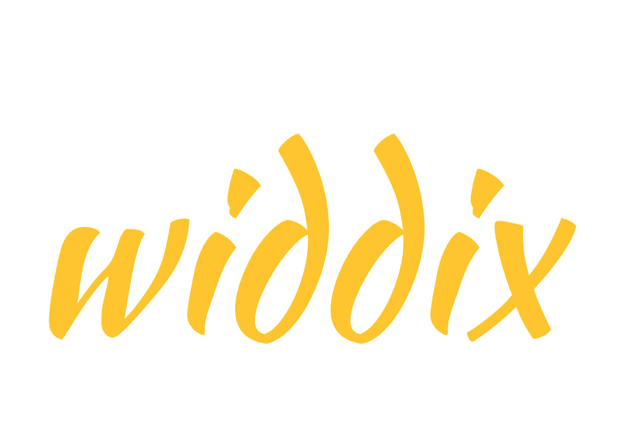
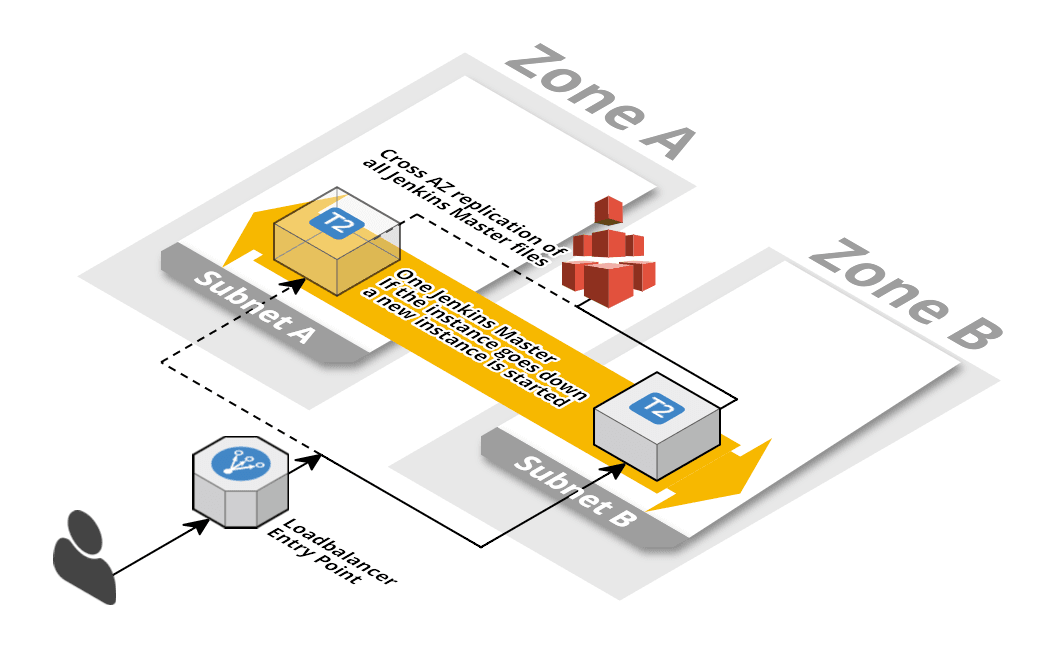
Jenkins 2.0: highly available master
This template describes a Jenkins master in a highly available manner. If the master instance fails it will be replaced automatically. All data stored on EFS where it is replicated across AZs and the file system can grow without a limit. The Jenkins master sits behind a load balancer to provide a fixed endpoint. Logs from the operating system and Jenkins are pushed to CloudWatch Logs.
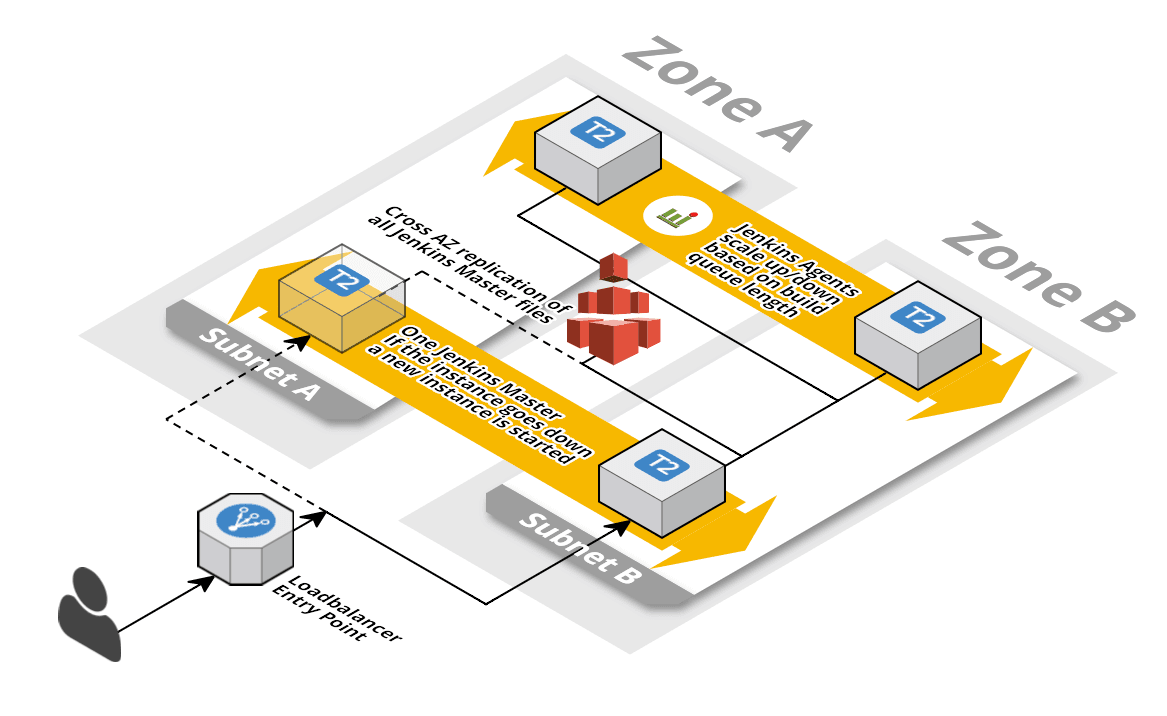
Jenkins 2.0: highly available master and dynamic agents
This template describes a Jenkins master in a highly available manner. If the master instance fails it will be replaced automatically. All data stored on EFS where it is replicated across AZs and the file system can grow without a limit. The Jenkins master sits behind a load balancer to provide a fixed endpoint. A dynamic pool of agents will execute builds. If the build queue grows new agents are provisioned. If the build queue is empty agents are taken offline (only if they have no build running). System logs and Jenkins logs are pushed to CloudWatch Logs.
Security: AWS Config setup
This template enables AWS Config to deliver an AWS resource inventory to S3. Allowing you to keep track of infrastructure changes for compliance and debugging of your cloud infrastructure.
Support
We offer support for our CloudFormation templates: setting up environments based on our templates, adopting templates to specific use cases, resolving issues in production environments. Hire us!
