Protect Amazon Connect from viruses and malware by scanning attachments
Four years ago, we stumbled into Amazon Connect. In essence, Amazon Connect allows your users to reach your organization represented by agents via phone or chat. While chatting, Amazon Connect allows users and agents to upload attachments. For many years, there was no good solution to ensure those files were malware-free. Given that anonymous users can start Amazon Connect chats, that’s quite scary. Lucky us, Amazon Connect just released a feature that enables scanning of attachments for malware. You might think: “Great, Amazon Connect scans all files from now on”. But no, Amazon Connect enables you to scan the attachments yourself. In other words, Amazon Connect invokes a Lambda function that you run to check if a file is clean or infected. If your Lambda function marks the file as clean, it will become visible to the other party. In the following blog post, I share what I learned while integrating our product bucketAV - Antivirus protection for Amazon S3 with Amazon Connect to scan files for malware.
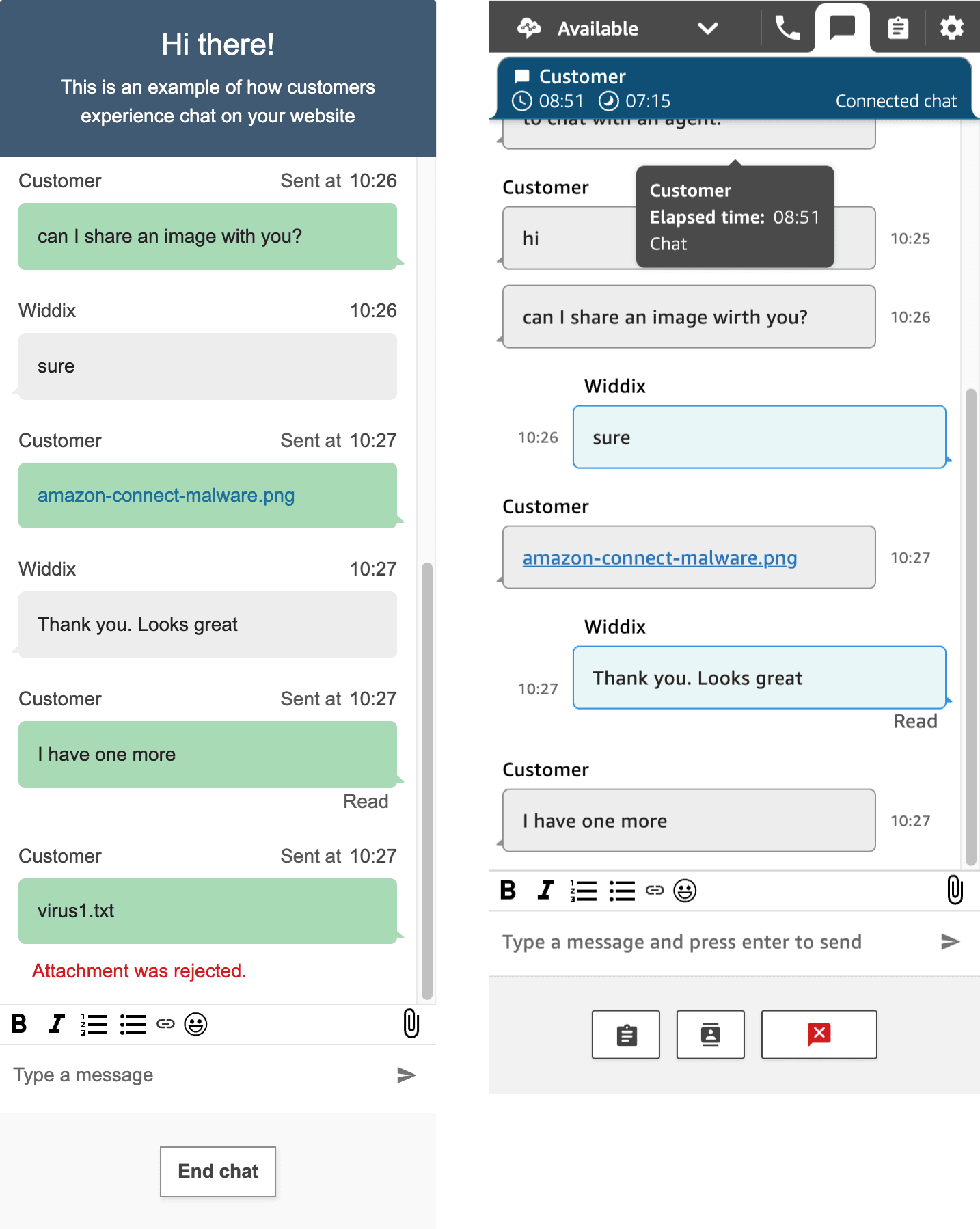
The following figure shows an interaction between a user and an agent. The user (on the left) uploads a clean file first, followed by a virus. The agent (on the right) only receives the clean file. The infected file gets blocked.
In the following, I share my code with you.
bucketAV customers can skip the rest of the blog post and use our Amazon Connect integration to scan attachments as documented here.
The contract
Amazon Connect calls the Lambda function with the following payload in a synchronous invocation:
{ |
The function is expected to return the following for clean files within 60 seconds:
{ |
For infected files:
|
Amazon Connect retries up to 3 times when a synchronous invocation returns an error. The maximum file size for an attachment to a case or a chat is 20MB.
The implementation
bucketAV scans files uploaded to Amazon S3 asynchronously. A scan job is submitted to an SQS queue, and bucketAV publishes the result to an SNS topic. Unfortunately, Amazon Connect follows a synchronous model. Therefore, I fall back to good old busy waiting to integrate bucketAV’s asynchronous model with Amazon Connect’s synchronous approach.
The first Lambda function is connected to the SNS topic where bucketAV publishes scan results. When a scan result is published, the Lambda function stores it in a DynamoDB table. The environment variable TABLE_NAME is used to pass the name of the DynamoDB table that stores scan results.
// connect-subscription.js |
The second Lambda function is the one invoked by Amazon Connect. When an attachment is uploaded, the Lambda function:
- Submits a scan job to the SQS queue.
- Queries the DynamoDB table every second until a scan result is available (remember, the first Lambda function stores the scan result).
- Returns APPROVED for clean files or REJECTED for infected files as Amazon Connect expects.
The environment variableTABLE_NAMEis the same as for the first Lambda function.SCAN_QUEUE_URLreferences the URL of the SQS queue that enqueues scan jobs. I also useSTACK_NAMEto reference the CloudFormation stack name that deploys the Lambda function.
// connect.js |
The following AWS infrastructure is required:
- DynamoDB Table.
- IAM roles for both Lambda functions.
- Lambda functions.
- SNS subscription for the first Lambda function.
- Permission for the first Lambda function to allow SNS to invoke the function.
The following code is used to deploy the application with the AWS CDK:
const { CfnParameter, CfnCondition, CfnOutput, Fn, Aws } = require('aws-cdk-lib'); |
That’s it. I hope my blog post helps you to integrate your antivirus solution with Amazon Connect. If you don’t have an existing antivirus solution for AWS, check out bucketAV and the new Amazon Connect attachment scanning integration.
