Show your Tool: awsume
In this series, we present AWS tooling from the community for the community. We talk directly with the tool makers. Who are they? What problem does the tool solve? And what motivates them to contribute to open-source AWS tooling.

This time, we talk with Michael Barney about awsume. You can find Michael on GitHub and Twitter. Michael also has a website.
cloudonaut: Tell us a little about yourself, your history with AWS, and your motivation to develop AWS tooling.
Michael Barney: After college, I started at Trek10, an AWS consulting partner specializing in serverless. It was there that I discovered a passion for Serverless. As of writing, I’ve been working with AWS for about two years. I believe that the more AWS tooling evolves, the more enabled developers will be. The tool I’ve worked on, awsume, has helped the team at Trek10 a ton.
cloudonaut: What problem does your tool solve?
Michael Barney: awsume‚ is a command-line tool that grabs AWS credentials (access keys, session token, etc.) and exports them to environment variables. It makes MFA much easier to use, it’s extensible, and it comes with a few cool built-in utilities such as autoawsume, which automatically refreshes your credentials for you in the background.
cloudonaut: Who should use your tool? Who should not?
Michael Barney: The motivation behind the tool was that since the AWS CLI would use the MFA token on the assume-role call, you would have to re-enter your MFA token every hour. What you can do instead is make the get-session-token call on the source profile, which returns MFA credentials that are valid for 12 hours, so you can use those credentials every hour to renew your role credentials, without needing to re-enter your MFA token.
Trek10 does work in multiple accounts for each of our clients, so another motivation behind awsume is that maintaining your config and credentials files became cumbersome. awsume helped in that aspect by being extensible, so we developed a plugin to inject those profiles from our internal database at runtime.
Long story short, awsume is meant to be used by anyone who needs to access an aws account. Whether you’re part of a large complex organization or a hobbyist with a personal account, awsume could definitely help you out.
cloudonaut: Show us a short demo of your tool
Michael Barney: Please check out this short demo.
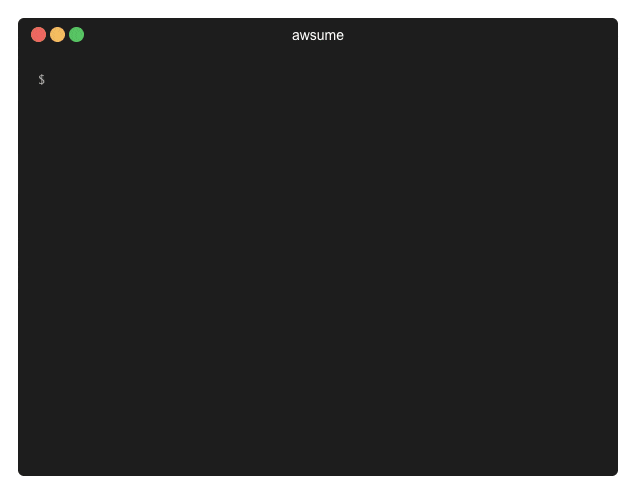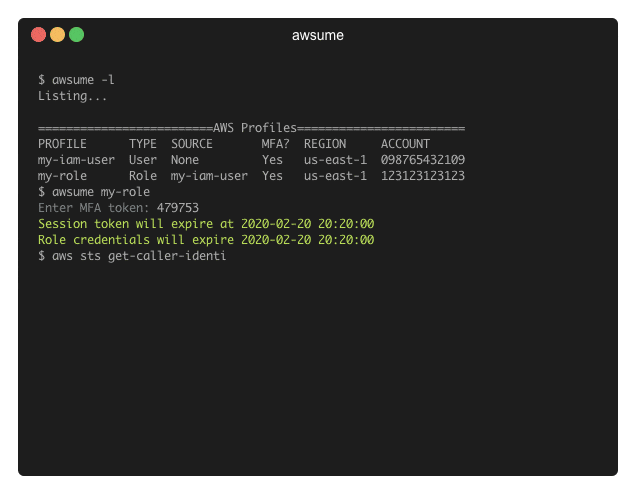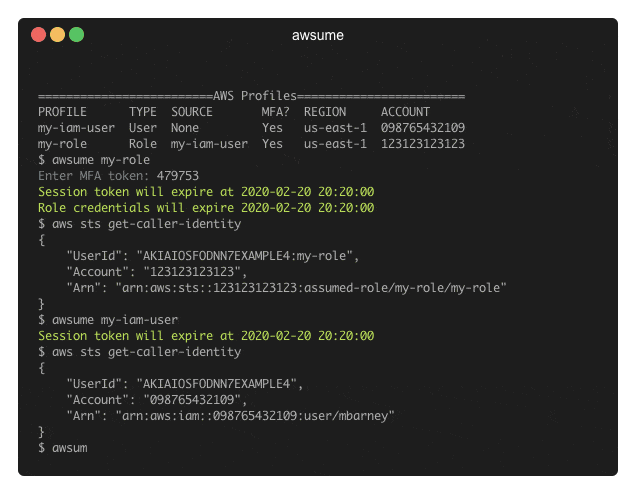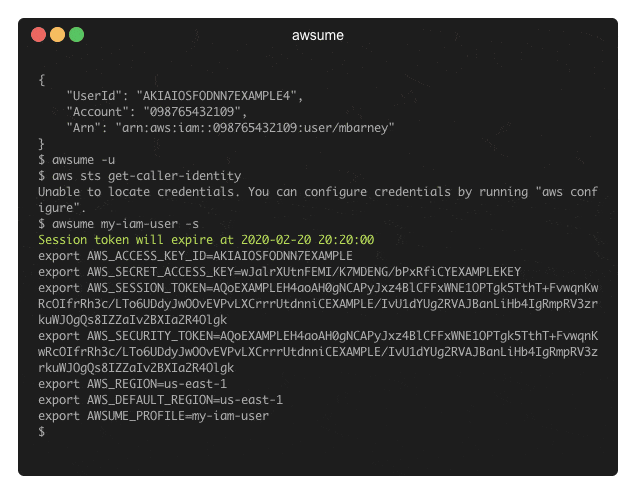
Basically, you run awsume <profile_name>, but there’s plenty of other ways to use awsume. Check out the documentation to learn about all features.
cloudonaut: How can we use your tool?
Michael Barney: Follow the quickstart guide at https://awsu.me/general/quickstart.html.
On most machines, you should be able to pip install awsume, restart your terminal, and it’ll work.
cloudonaut: Where can we find more information about your tool?
Michael Barney: I would check out the awsume website.
cloudonaut: Are you aware of tools that solve a similar problem than yours? What’s the difference?
Michael Barney: There are a few, namely aws-vault. As someone that hasn’t used it, it’s hard to talk about the differences, but I do know that aws-vault stores your credentials in the macOS Keychain, Windows Credential Manager, etc. as opposed to the default config and credentials files.
cloudonaut: What’s the roadmap for your tool? Are you planning any significant releases?
Michael Barney: There isn’t a public roadmap. You could check the GitHub repo for open issues and feature requests, so if you want it to do something that it doesn’t already, feel free to open an issue.
cloudonaut: How do you stay motivated to maintain your open source project?
Michael Barney: Working at a company that encourages best practices and thought leadership like Trek10, it’s pretty easy to stay motivated. I love good software.
cloudonaut: Are you attending any conferences within the next few months where the community can get in touch?
Michael Barney: I should be attending ServerlessConf this year.
–
What tools do you use to make your AWS work easier? Share your favorite tool with us!
Further reading
- Article Show your Tool: AWSInfo
- Article Show your Tool: Jenkins Pipeline Step Plugin for AWS
- Article Show your Tool: Parliament
- Tag iam
