#iam | AWS Identity and Access Management (1)
Controlling access to your cloud resources is key to protect your infrastructure from leaking data or malicious access.
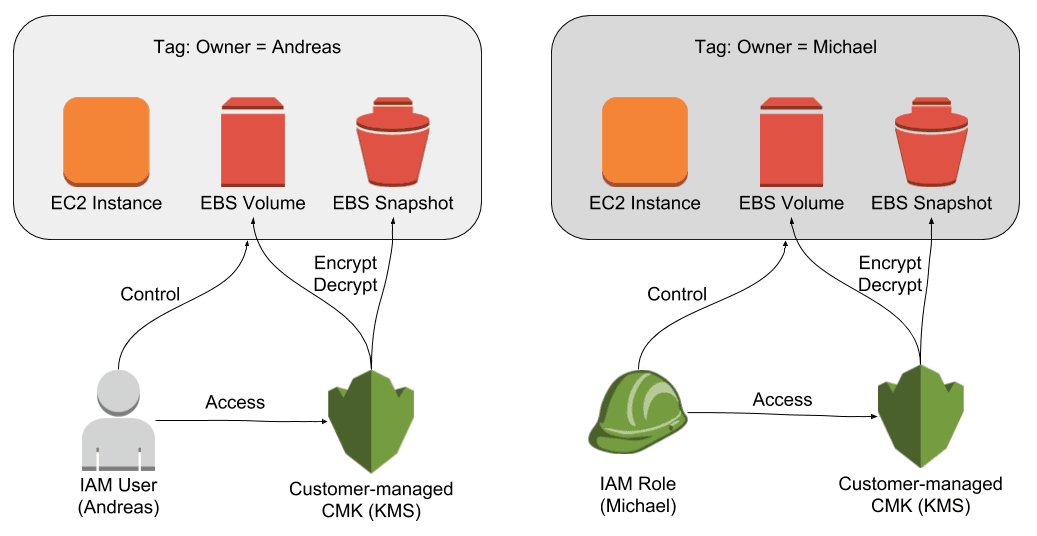
KMS Key Policy Privilege Escalation
Encrypting data at rest is a widespread best practice on AWS. In 2019, Werner Vogels set the tone with his motivational slogan, “Dance like nobody’s watching. Encrypt like everyone is!”. AWS shipped the ability to encrypt data at rest for almost all its...
Read moreHot off the Cloud: October 2022
What happened at AWS in October 2022? This is our summary and analysis of the announcements that interested us. In November, re:Invent, AWS’ major conference, will take place in Las Vegas. During re:Invent, AWS will announce many new features and servic...
Read moreEnhance EFS file system protection with TLS and IAM
Two significant aspects of data security are access restriction as well as confidentiality. In the following, you will learn two techniques to increase the security of data stored on an EFS file system (Amazon Elastic File System): enabling encryption o...
Read moreAWS Security: Stephen Kuenzli and Andreas Wittig on IAM
Stephen Kuenzli and I lead several cloud migration projects. In this conversation, we shared our learnings focusing on AWS security and IAM (Identity and Access Management). The result is advice and inspiration that will help you in your daily work. Our...
Read moreDefining IAM Policies with Terraform safely
Are you still defining IAM policies using heredoc syntax (<<EOF ... EOF) or jsonencode()? You can do better! As a result, terraform validate can tell you about typos before you apply them, and you get better auto-complete support from your IDE. Re...
Read moreHow to configure SAML for AWS SSO?
AWS SSO is a great way to grant engineers access to AWS accounts. By default, AWS SSO comes with a built in user database. However, it is also possible to configure identity federation via SAML. Doing so allows you to re-use existing users and groups. ...
Read moreHave you replaced IAM Users with AWS SSO yet?
The most secure option to isolate workloads from each other is to use multiple AWS accounts. Many organizations use different AWS accounts for testing and production, for example. The more AWS accounts you use, the more complicated it gets to manage use...
Read moreRecord AWS API calls to improve IAM Policies
Have you ever looked at an IAM policy and wondered: Is it really necessary to grant access to this specific action? Or do you need to know which API calls a legacy or 3rd party application is actually sending to come up with a secure IAM policy? CloudTr...
Read moreUse multiple AWS accounts, but keep it simple!
Getting started with AWS is a challenge. Unlimited possibilities, competing solutions, and distractions. Even the first step to create an AWS account requires careful planning. AWS marketers promote the AWS Landing Zone solution. Consulting partners add...
Read moreAWS Account Structure: Think twice before using AWS Organizations
What is an AWS account? I like to use the following two ways to describe the concept of an AWS account: a tenant in Amazon’s multi-tenant cloud or a virtual data center. When running multiple workloads and environments using numerous AWS accounts is the...
Read moreShow your Tool: Parliament
In this series, we present AWS tooling from the community for the community. We talk directly with the tool makers. Who are they? What problem does the tool solve? And what motivates them to contribute to open-source AWS tooling. This time, we talk wit...
Read moreShow your Tool: Jenkins Pipeline Step Plugin for AWS
In this series, we present AWS tooling from the community for the community. We talk directly with the tool makers. Who are they? What problem does the tool solve? And what motivates them to contribute to open-source AWS tooling. This time, we talk wit...
Read moreShow your Tool: awsume
In this series, we present AWS tooling from the community for the community. We talk directly with the tool makers. Who are they? What problem does the tool solve? And what motivates them to contribute to open-source AWS tooling. This time, we talk wit...
Read moreAvoid the 60 minutes timeout when using the AWS CLI with IAM roles
You can configure the AWS CLI to assume an IAM role for you in combination with MFA. If you are a power user of the CLI, you will realize that you have to enter your MFA token every 60 minutes, which is annoying. You will learn how to fix that in the f...
Read moreEC2 Instance Connect is an insecure default!
Two months before, Michael wrote about why AWS SSM is a trojan horse. Shortly after that, AWS released EC2 Instance Connect, which is even worse. If you use Amazon Linux 2 or Ubuntu, the chances are high that everyone in your AWS account can SSH into ev...
Read moreAWS SSM is a trojan horse: fix it now!
Recently, I held a security workshop together with a team of engineers. At some point, the team demonstrated how they use AWS Systems Manager (SSM) to run commands on a machine. What the team didn’t know: they enabled a backdoor that allows everyone wit...
Read moreMy mental model of AWS
AWS is a complex system that no one can understand end-to-end? As AWS professionals we still have to deal with the AWS system daily. We design for AWS, and we debug our applications running in AWS. How can we deal with a system that is too complex to un...
Read moreRestricting Access to EC2 Instances Based on Tags
The principle of least privilege is key when it comes to securing your infrastructure on AWS. For example, an engineer should only be able to control EC2 instances that are in scope for her day-to-day work. But how do you make sure an engineer is only a...
Read moreAWS Security Primer
I was preparing some AWS Security related training. Soon, I realized that this topic is too huge to fit into my brain. So I structured my thoughts in a mind map1. Within a couple of minutes2 I came up with this: What is your first reaction? Mine was pr...
Read moreComplete AWS IAM Reference
Writing IAM policies is hard. Following the principle of least privilege is even harder. To write a secure IAM policy you need to know: What actions are needed? Are resource-level permissions supported and on what levels? Are conditions supported to re...
Read more