#iam | AWS Identity and Access Management (2)
Controlling access to your cloud resources is key to protect your infrastructure from leaking data or malicious access.
Your AWS Account is a mess? Learn how to fix it!
Have you no wildcard ec2:* in your IAM policies? Your Security Group rules are as strict as possible? Your S3 Bucket Access Policies only contain rules you know? You know about every single resource that runs in your account? If so, stop reading and ple...
Read moreAvoid security credentials on GitHub
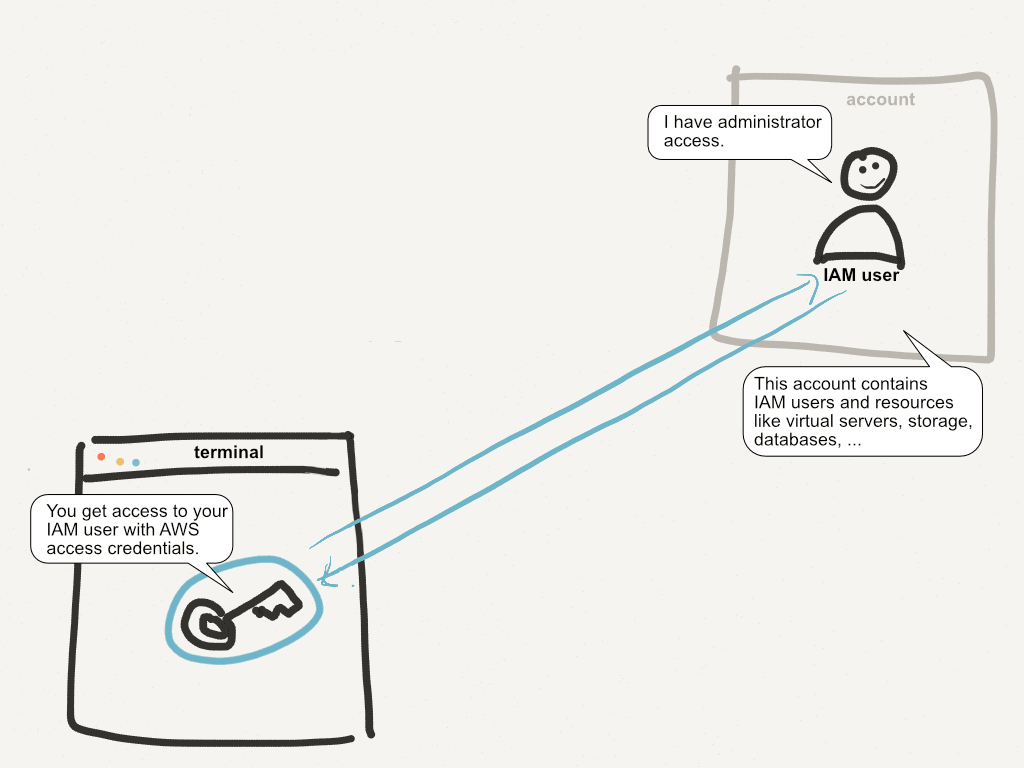
Your AWS account is a valuable target for bad guys. With access to your security credentials an attacker is potential able to steal sensitive data, utilize resources on your costs, or sabotage your infrastructure. Two years ago AWS and their customers o...
Read moreManage AWS EC2 SSH access with IAM
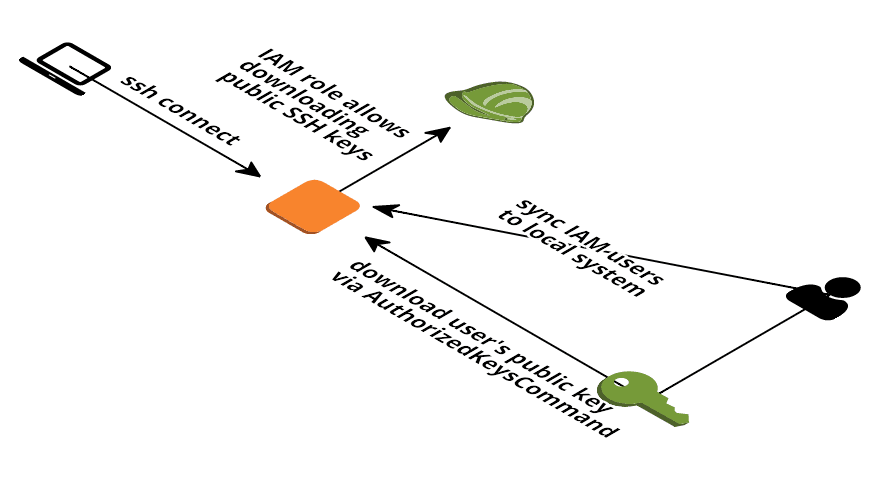
AWS can deploy one EC2 Key Pair to your EC2 instance. But this approach has several disadvantages: You can only use one key per EC2 instance. But you shouldn’t share keys between users. Access to EC2 instances via SSH can not be restricted to specific ...
Read moreCloudFormation vs Engineers: How to protect your CloudFormation managed AWS account from human intervention
To eliminate human error as much as possible I advised you to follow the idea of Infrastructure as Code implemented by AWS CloudFormation. Changes to your infrastructure like launching a new virtual server or making changes to a firewall configuration a...
Read moreYour single AWS account is a serious risk
Your AWS account is one of the most valuable things you own if you run a business on AWS. If you only own a single AWS account, you’re facing a serious security risk! The post will show you why this a problem and how you can solve it. This post receive...
Read more