AWS Monitoring with EventBridge
When it comes to AWS monitoring, you probably think of Amazon CloudWatch first. That’s right, but there is another source of information about the health of your cloud infrastructure: Amazon EventBdrige. In this blog post, you’ll learn how to tap into EventBridge to get important information about running your cloud infrastructure.
How to configure AWS Monitoring based on EventBridge?
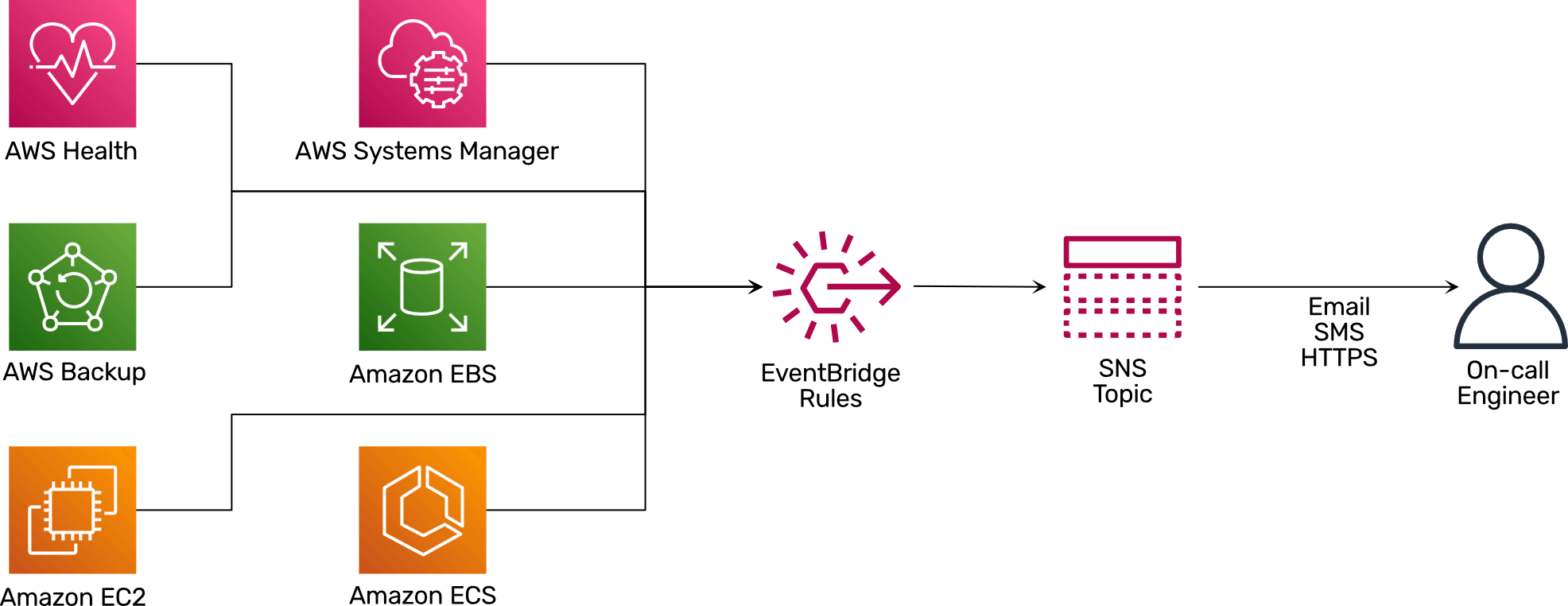
The following diagram shows what is needed to extend your AWS monitoring with the help of EventBridge.
- Services like AWS Backup, Amazon EC2, and AWS Health publish events when things go wrong or human intervention is necessary to EventBridge.
- EventBridge rules filter those events based on a pattern and forward matching events to an SNS topic.
- The SNS topic sends events to on-call engineers via Email, SMS, or HTTPS.
I have compiled some examples of EventBridge rules and event patterns for AWS monitoring in the following. The code snippets are written in Terraform configuration syntax, but the event patterns can also be used with CloudFormation or even in the AWS Management Console.
Monitoring AWS account root user login with EventBridge
The following EventBridge rule (formerly known as CloudWatch event rule) defined in Terraform configuration syntax ensures you are notified whenever someone uses the AWS account root user to log in.
resource "aws_cloudwatch_event_rule" "root_user_login" { |
Monitoring AWS Health announcements with EventBridge
Over the past years, AWS improved the AWS Health Dashboard and is using this channel to communicate outages as well as breaking changes to services. Getting notified about new issues helps ensure your cloud infrastructure’s continuity.
resource "aws_cloudwatch_event_rule" "health_issue" { |
Monitoring EC2 Auto Scaling with EventBridge
EC2 Auto Scaling launches instances, for example, to add capacity to a fleet. It is crucial to get notified if Auto Scaling fails to launch or terminate an instance, as human intervention is most likely required to fix the problem.
resource "aws_cloudwatch_event_rule" "auto_scaling_failed" { |
Monitoring EBS Snapshots with EventBridge
Do you rely on creating EBS snapshots for backing up data? If so, you should keep an eye on failed EBS snapshots by using the following EventBridge rule.
resource "aws_cloudwatch_event_rule" "ebs_failed" { |
Monitoring SSM Automation with EventBridge
The Systems Manager provides a toolkit to automate the management of EC2 instances. But will you notice when automation fails during the night? The following EventBridge rule will keep you posted.
resource "aws_cloudwatch_event_rule" "ssm_automation_failed" { |
Monitoring ECS Tasks with EventBridge
The Elastic Container Service (ECS) orchestrates containers. But sometimes containers fail and exit with an exit code > 0. The following EventBridge rule will ensure you are getting notified about the issue.
resource "aws_cloudwatch_event_rule" "ecs_task_failed_non_zero" { |
Monitoring ECR Image Scan with EventBridge
The Elastic Container Registry (ECR) comes with the capability to scan container images for known vulnerabilities. But how do you ensure you are notified about severe findings? Here you go.
resource "aws_cloudwatch_event_rule" "ecr_image_scan_finding" { |
Monitoring Amazon Certificate Manager (ACM) with EventBridge
We have all experienced downtimes caused by expired SSL/TLS certificates. This doesn’t have to be the case. Monitor the Amazon Certificate Manager (ACM) and get notified when certificates expire.
resource "aws_cloudwatch_event_rule" "acm_certificate_approaching_expiration" { |
Monitoring AWS Backup with EventBridge
Sometimes backup services like AWS Backup provide false security. After all, what happens if AWS Backup runs into errors when creating important backups? You can use the following EventBridge rule to catch backup errors.
resource "aws_cloudwatch_event_rule" "backup_failed" { |
Monitoring Elastic Beanstalk with EventBridge
Elastic Beanstalk is a popular service for deploying web applications on AWS. It would help if you were the first to know about a problem with your application. The following EventBridge rule notifies you about issues with your Elastic Beanstalk applications.
resource "aws_cloudwatch_event_rule" "elastic_beanstalk_failed" { |
Summary
When it comes to AWS monitoring, EventBridge is an essential source of information. Ensure you are using EventBridge rules forwarding events to an SNS topic to get notified about issues with your cloud infrastructure.
All examples from this blog post originate from marbot-io/terraform-aws-marbot-monitoring-basic.
Also, please check out our product marbot to roll out monitoring based on CloudWatch and EventBridge with ease.
