Getting Started with Free Templates for AWS CloudFormation
Writing CloudFormation templates from scratch is a lot of work. You will run into many issues along the way: the documentation is incomplete, magic values are required, unsupported combinations of attributes, etc. The feedback cycles are long. In the end, we have to provision real infrastructure to test the template. If you ever created an Elastisearch cluster, you feel the pain. We also observe that AWS architectures follow similar patterns (aka best practices). So why not make a collection of templates and share them with the world? That’s what we did in late 2015. We launched Free Templates for AWS CloudFormation. In this blog post, I provide you an overview of the project and show you typical use cases.

You can speed up development and migration projects by reusing our templates to create complex environments for everyday use cases with ease. All templates are peer-reviewed by an expert and verified with automated tests. We even go one step further. All templates are production-ready.
Do you prefer listening to a podcast episode over reading a blog post? Here you go!
Production-ready
If no other limitations are documented, the following applies:
- Highly available: The template has no single point of failure.
- Scalable: The capacity increases or decreases based on utilization (auto-scaling).
- Frictionless deployment: You can deploy new versions of the templates or your application without downtime.
- Secure: We use the latest operating systems and software components. We follow the least privilege principle in all areas (IAM, network). We support encryption. We enable backups.
- Operator-friendly: Logging, monitoring, and alerting are configured out-of-the-box.
Let’s see what you can build with our templates.
Use cases
Our templates are designed in a reusable way. Most templates depend on other templates. In many cases, you need to create a VPC first.
VPC setup
Many AWS workloads run on a VPC setup like this:
- Three public subnets
- Three private subnets
- access to the Internet via NAT gateways
- access to the AWS API via endpoints
- VPC Flow Logs to record network activity
- VPN bastion host that admins/devs can use to access EC2 instances, RSD databases, etc. from local machines
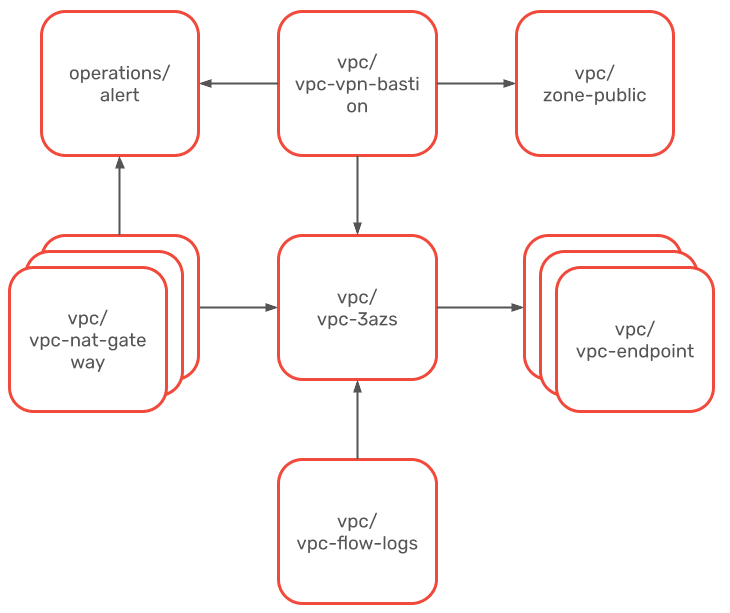
To deploy this architecture, start with a template that has no dependencies (no outgoing arrows). Once the CloudFirmation stacks are created, you can continue with the rest of the templates. Those templates with dependencies have parameters that start with Parent. The value is the CloudFormtion stack name that you want to link this new stack with.
The cool thing is that you can re-use the dependencies. E.g., you can use the same VPC for many different workloads.
Used templates:
- operations/alert
- vpc/vpc-3azs
- vpc/vpc-nat-gateway
- vpc/vpc-vpn-bastion
- vpc/vpc-endpoint-s3
- vpc/vpc-endpoint-dynamodb
- vpc/vpc-endpoint
- vpc/vpc-flow-logs
- vpc/zone-public
You can also run real workloads with our templates.
Containerized app
There are many options to run containerized workloads on AWS. We recommend using ECS Fargate. Templates for a large collection of datastores exist as well. In this case, we use RDS. Additionally, we take care of DNS, alerting, and the VPN connection to the database for your team.
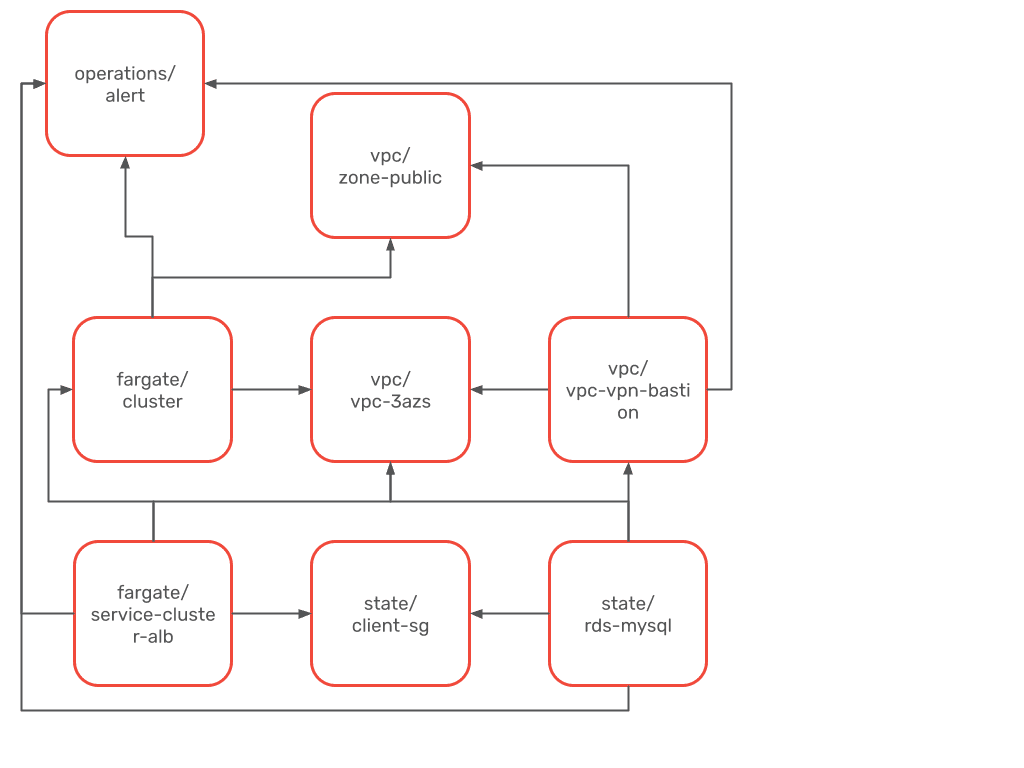
Used templates:
- operations/alert
- vpc/vpc-3azs
- vpc/vpc-vpn-bastion
- fargate/cluster
- fargate/service-cluster-alb
- state/client-sg
- state/rds-mysql
- vpc/zone-public
Check out the following template catalog to get an idea of what we support.
Template catalog
The following templates are available:
- Elastic Compute Cloud (EC2)
- EC2 Container Service (ECS)
- Fargate
- Jenkins
- Operations
- Security
- State / Data
- Static Website
- Virtual Private Cloud (VPC)
- VPC with private and public subnets in two Availability Zones
- VPC with private and public subnets in three Availability Zones
- VPC with private and public subnets in four Availability Zones
- NAT Gateway
- NAT instance
- SSH bastion host/instance
- VPN bastion host/instance
- Gateway Endpoint (S3)
- Gateway Endpoint (DynamoDB)
- Interface Endpoint
- VPC Flow Logs to CloudWatch Logs
- Public DNS Zone
- Private DNS Zone
- DNSSEC
- WordPress
All templates are published under Apache License Version 2.0. Become a sponsor or contributor and support the project!
