Category Security (Page 1)
AWS Security Primer
I was preparing some AWS Security related training. Soon, I realized that this topic is too huge to fit into my brain. So I structured my thoughts in a mind map1. Within a couple of minutes2 I came up with this: What is your first reaction? Mine was pr...
Read moreImprove Security (Groups) using VPC Flow Logs & AWS Config
As mentioned in the previous post Your AWS Account is a mess? Learn how to fix it!, most AWS accounts are a mess. This can be a serious risk, especially for security-related resources like Security Groups. In this post, we will describe a technique to m...
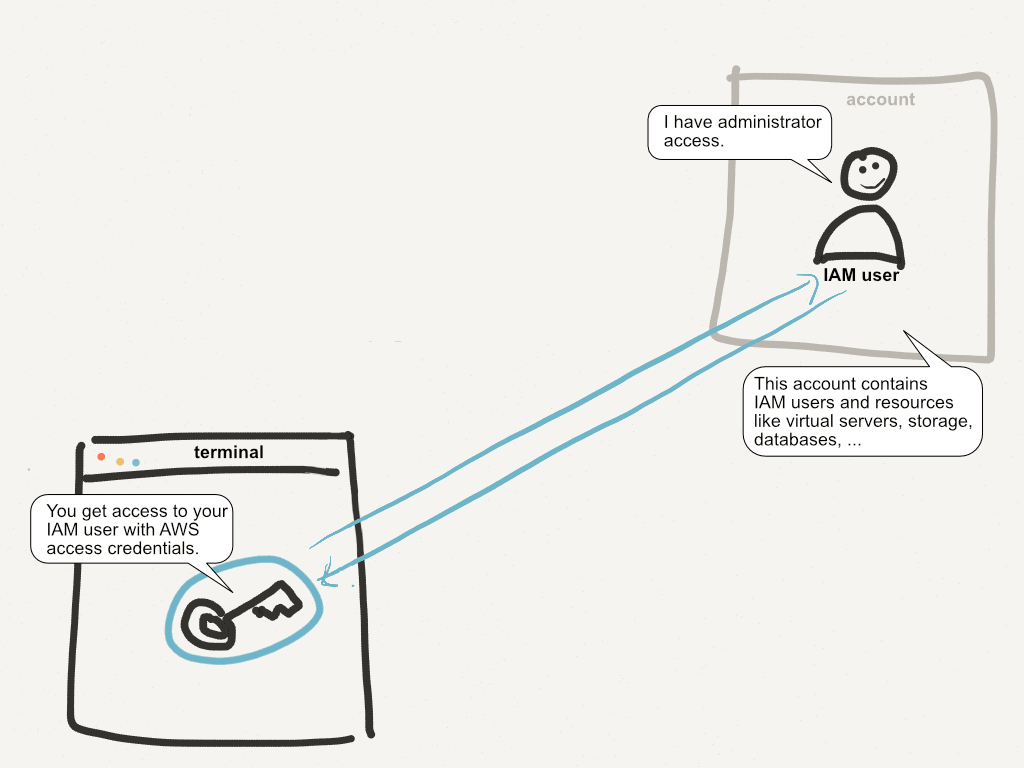
Read moreComplete AWS IAM Reference
Writing IAM policies is hard. Following the principle of least privilege is even harder. To write a secure IAM policy you need to know: What actions are needed? Are resource-level permissions supported and on what levels? Are conditions supported to re...
Read moreDevOps and Security #c9d9
What are some of the best practices for building security as an integral part of your tools and practices throughout your delivery pipeline? On Tuesday I participated in an online panel on the subject of DevOps and Security, as part of Continuous Discus...
Read moreDIY AWS Security Review
A regular security review of your AWS account can reveal security issues with little effort. There are some very easy things you can automatically check with the help of the AWS Command Line Interface that have a big impact. Limit network traffic from 0...
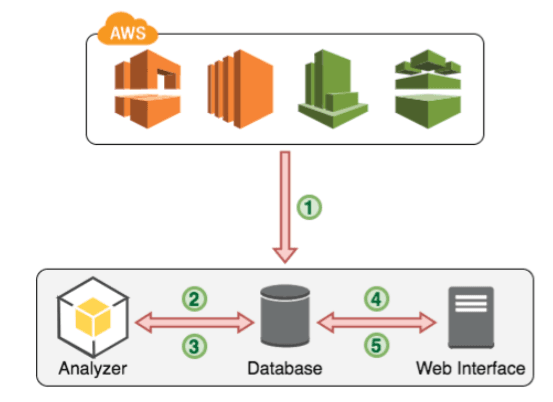
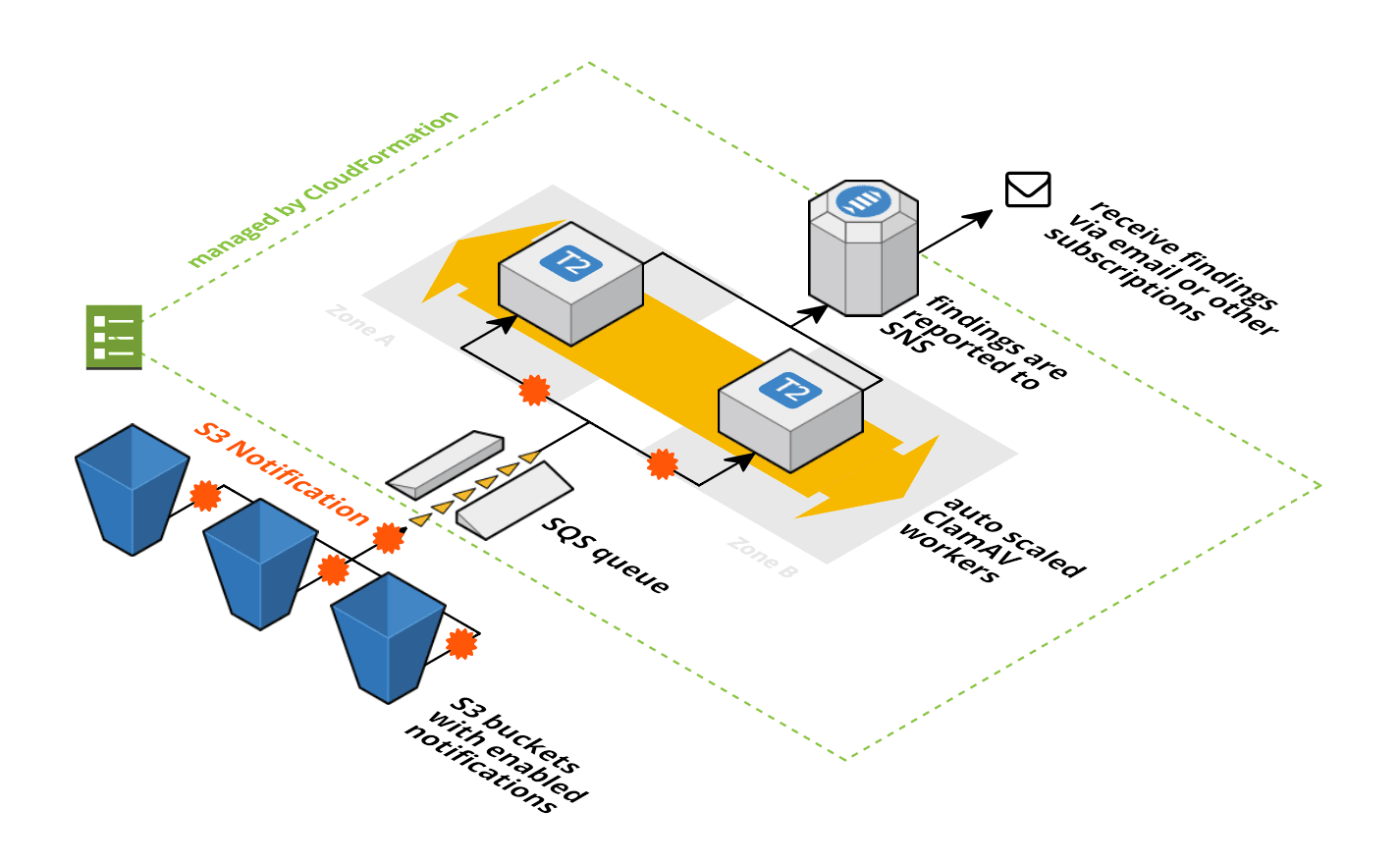
Read moreAntivirus for S3 Buckets
Many of our AWS consultancy clients ask me: “How can we make sure that the files that we store on S3 are virus free?” As always, our clients are looking for simple and cheap solutions. That’s why we developed Antivirus for Amazon S3. Every file that i...
Read moreEvent Driven Security Automation on AWS
If your developers create their own infrastructure in minutes, who cares about security? In some organizations the security teams become the new bottleneck if the company wants to deploy every commit to production. Because manual reviews can’t be done f...
Read more5 AWS mistakes you should avoid
Since this year I’m working as an AWS Cloud Consultant where I see a lot of small to medium sized AWS deployments. Most of them are typical web applications. I want to share with you the 5 most common mistakes that you better avoid: managing infrastruc...
Read moreImprove AWS security: protect your keys with ease
As a DevOps engineer, I love to work with the AWS Command Line Interface (CLI) to control various AWS resources in an (half-)automated way. To be able to do so it is necessary to store access keys on my local machine. These access keys (access key ID an...
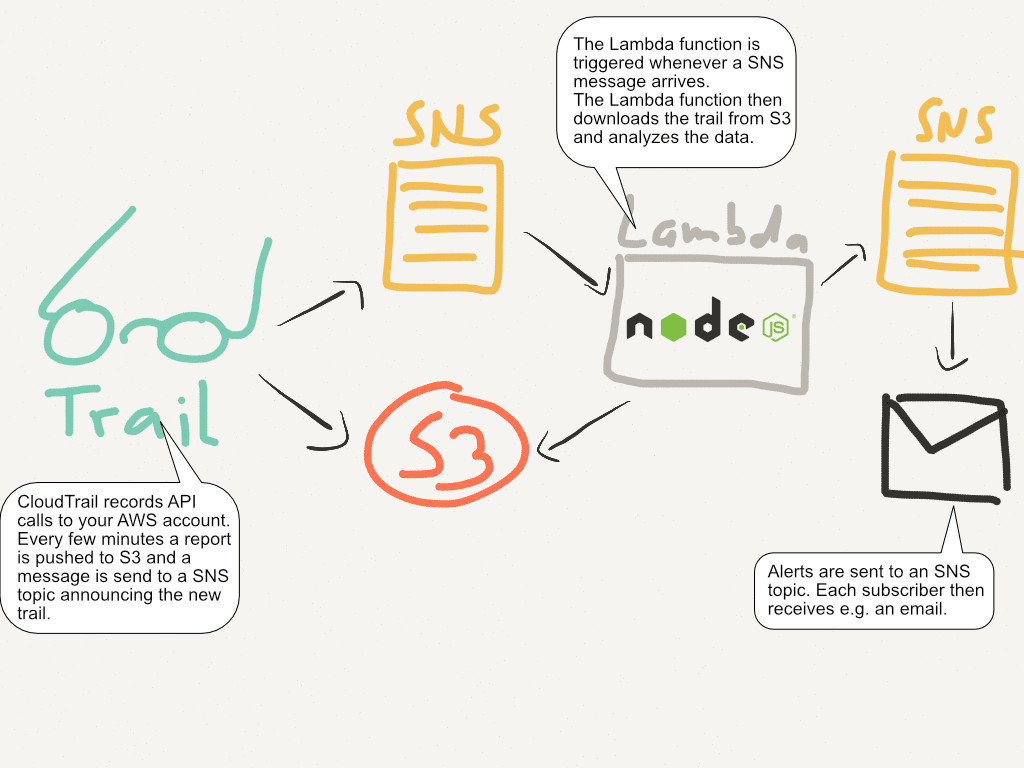
Read moreMonitor your AWS account to detect suspicious behavior in real time
You can track every change made to your AWS account with CloudTrail. Did you know that you can also monitor your AWS account in near real time with custom rules specific to your use case? By combining CloudTrail, S3, SNS, and Lambda, you can run a piece...
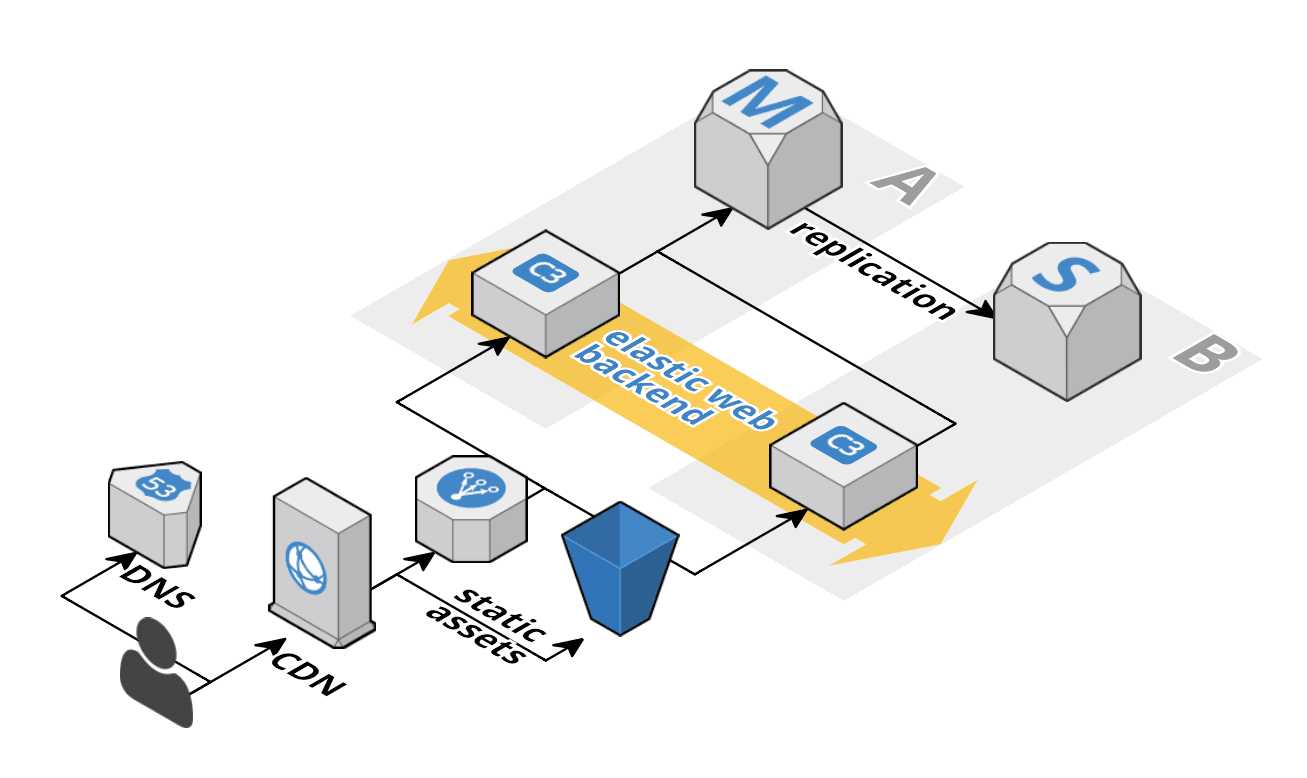
Read moreYour single AWS account is a serious risk
Your AWS account is one of the most valuable things you own if you run a business on AWS. If you only own a single AWS account, you’re facing a serious security risk! The post will show you why this a problem and how you can solve it. This post receive...
Read more