Does your VPC endpoint allow access to half of the Internet?
Are you using VPC endpoints to enable private connections between your VPC and AWS services? Drop everything and check the policy attached to your VPC Endpoint for S3. You might have allowed access to half of the Internet - assuming that half of the Internet is hosted on S3 - from your private network accidentally.

The Problem
By default, a VPC endpoint for S3 allows access to all S3 buckets. So an EC2 instance running in your VPC has access to all S3 buckets worldwide. Not only the S3 buckets you own but also the S3 buckets owned by other AWS customers. For example, anyone with access to your VPC could copy data from your systems to S3 buckets owned by someone else. Of course, the other way round - downloading data from S3 aka. half of the Internet - is possible as well.
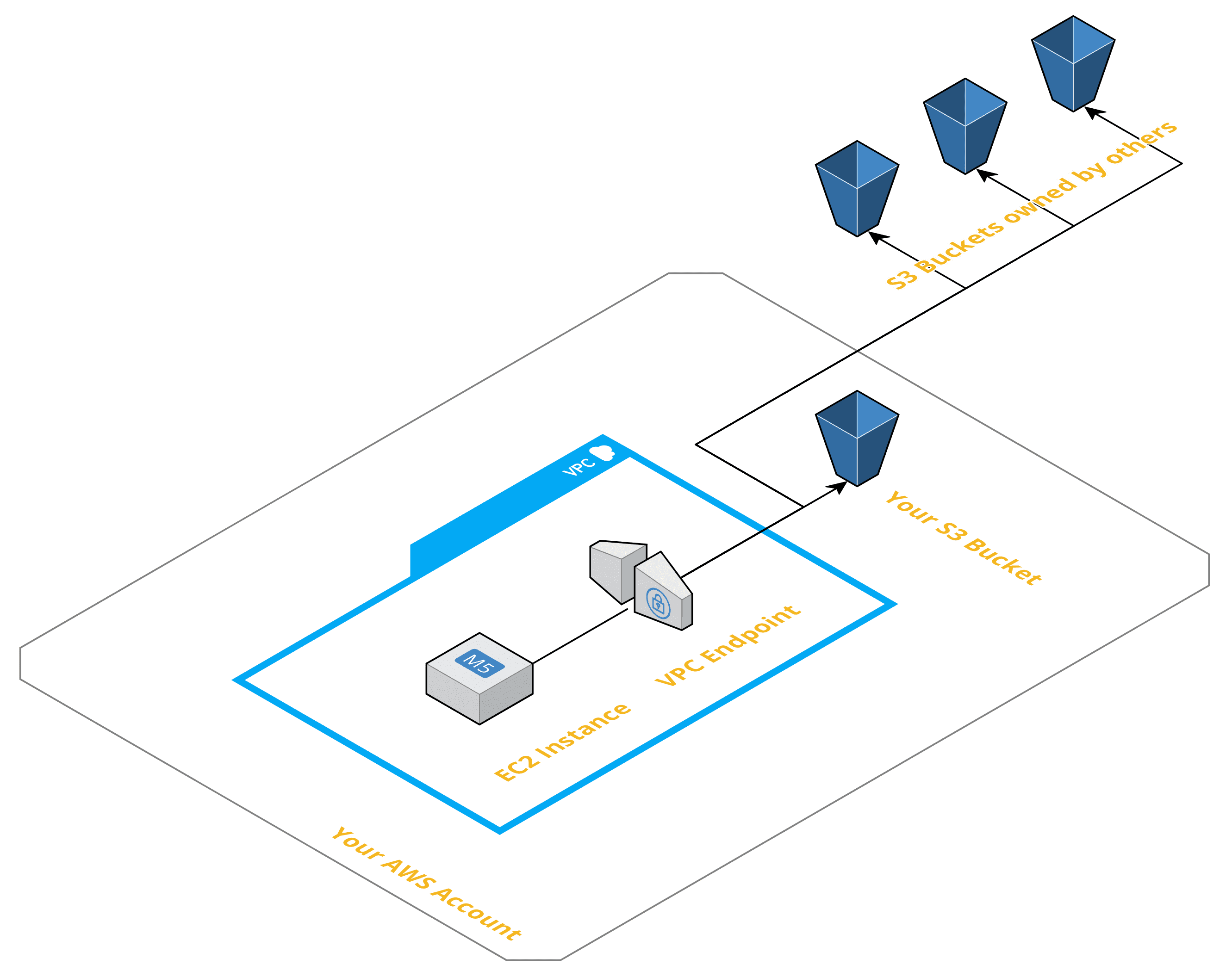
The Solution
By attaching an endpoint policy to your VPC endpoint for S3, you can restrict the usage of the endpoint to certain S3 buckets. I came up with the following endpoint policy recently, which allows access to all S3 buckets owned by your AWS account. In my opinion, a good tradeoff limiting access and configuration overhead.
Make sure to replace 111111111111 with your AWS account ID.
{ |
Warning: In case you need to access S3 buckets from your VPC that you do not own, you need to extend the endpoint policy. That’s example the case for S3 buckets offered by AWS.
That’s it. Don’t forget, details are important!
Further reading
- Article 5 good reasons not to get AWS certified
- Article Unboxing Amazon Managed Service for Prometheus (AMP)
- Article What's new about AWS SDK for JavaScript v3?
- Tag vpc
- Tag security
- Tag s3
