#security | Cloud Security (3)
All about the shared responsibility model in the cloud. Includes topics like networking (VPC), authentication and authorization (IAM), and more.
DIY AWS Security Review
A regular security review of your AWS account can reveal security issues with little effort. There are some very easy things you can automatically check with the help of the AWS Command Line Interface that have a big impact. Limit network traffic from 0...
Read moreAvoid security credentials on GitHub
Your AWS account is a valuable target for bad guys. With access to your security credentials an attacker is potential able to steal sensitive data, utilize resources on your costs, or sabotage your infrastructure. Two years ago AWS and their customers o...
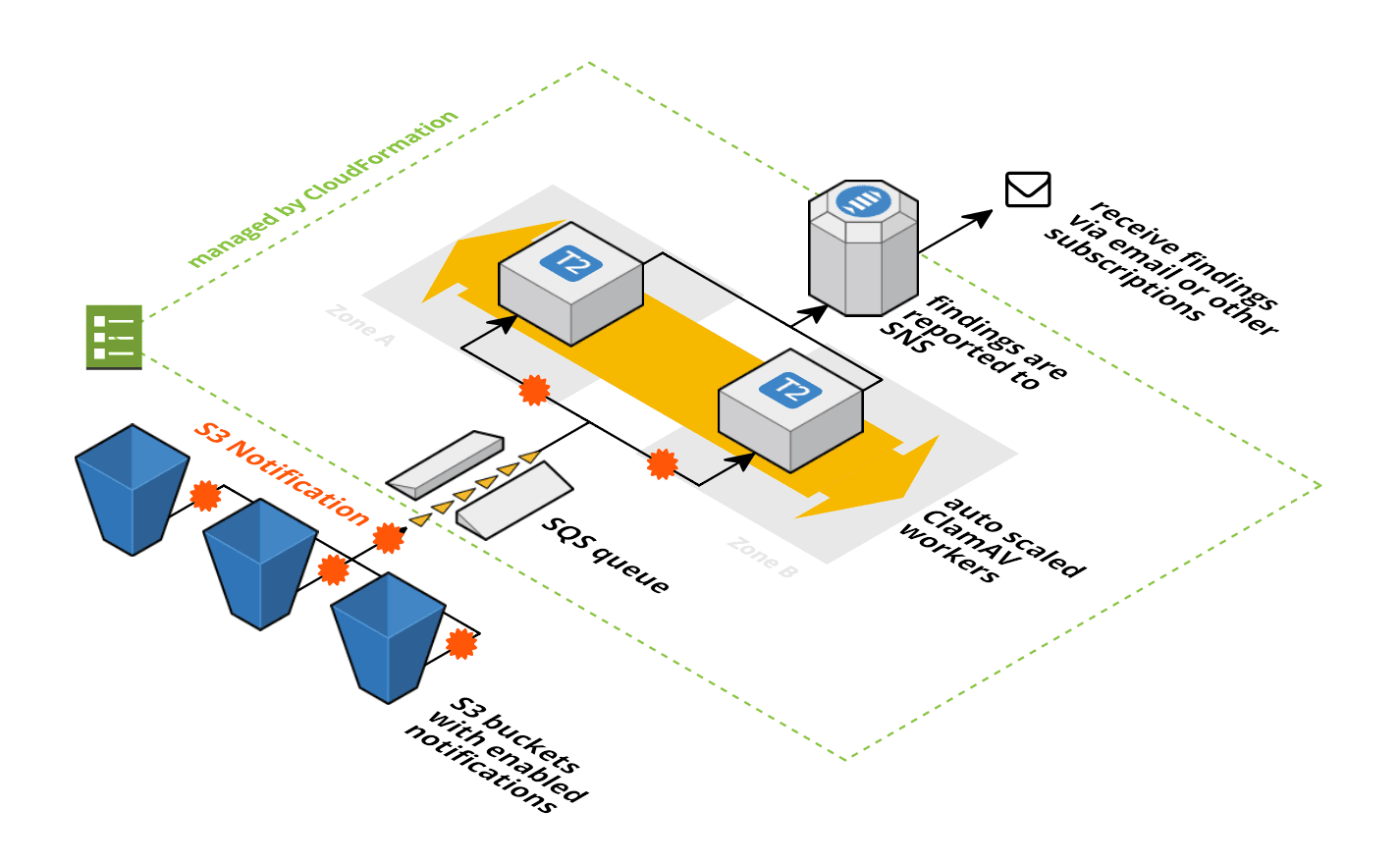
Read moreAntivirus for S3 Buckets
Many of our AWS consultancy clients ask me: “How can we make sure that the files that we store on S3 are virus free?” As always, our clients are looking for simple and cheap solutions. That’s why we developed Antivirus for Amazon S3. Every file that i...
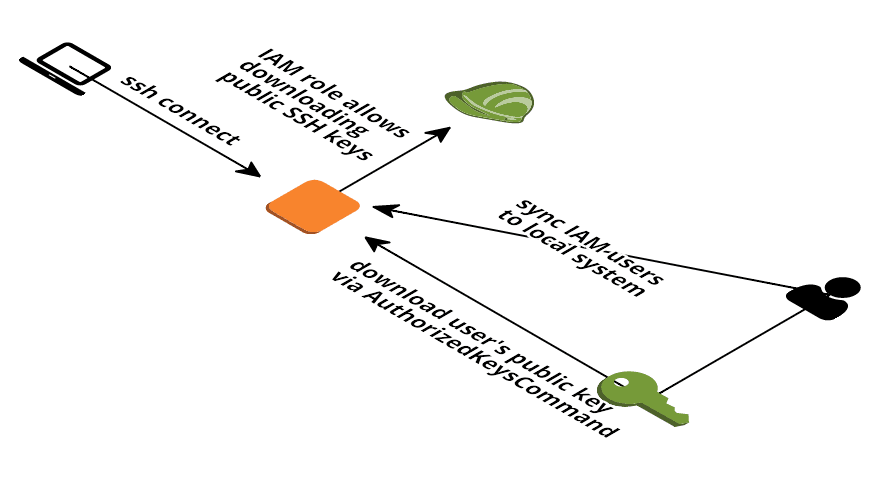
Read moreManage AWS EC2 SSH access with IAM
AWS can deploy one EC2 Key Pair to your EC2 instance. But this approach has several disadvantages: You can only use one key per EC2 instance. But you shouldn’t share keys between users. Access to EC2 instances via SSH can not be restricted to specific ...
Read moreEvent Driven Security Automation on AWS
If your developers create their own infrastructure in minutes, who cares about security? In some organizations the security teams become the new bottleneck if the company wants to deploy every commit to production. Because manual reviews can’t be done f...
Read moreSecurity Templates for AWS CloudFormation
This page has moved to GitHub: https://github.com/widdix/aws-cf-templates/tree/master/security
Read moreAvoid Sharing Key Pairs for EC2
Lock and key devices are used by mankind for more than 6.000 years. Whether mechanical, electrical or digital, the concept stays the same: a key is needed to access resources behind a lock. Technology has made incredible progress since then. But one pro...
Read moreImprove AWS security: protect your keys with ease
As a DevOps engineer, I love to work with the AWS Command Line Interface (CLI) to control various AWS resources in an (half-)automated way. To be able to do so it is necessary to store access keys on my local machine. These access keys (access key ID an...
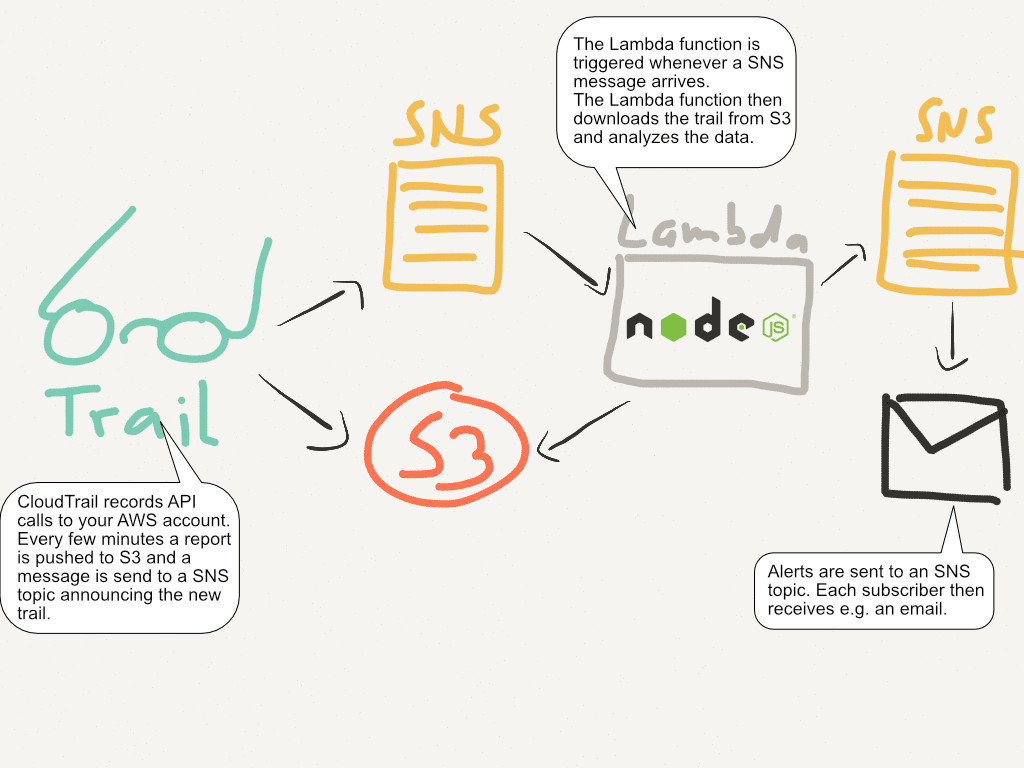
Read moreMonitor your AWS account to detect suspicious behavior in real time
You can track every change made to your AWS account with CloudTrail. Did you know that you can also monitor your AWS account in near real time with custom rules specific to your use case? By combining CloudTrail, S3, SNS, and Lambda, you can run a piece...
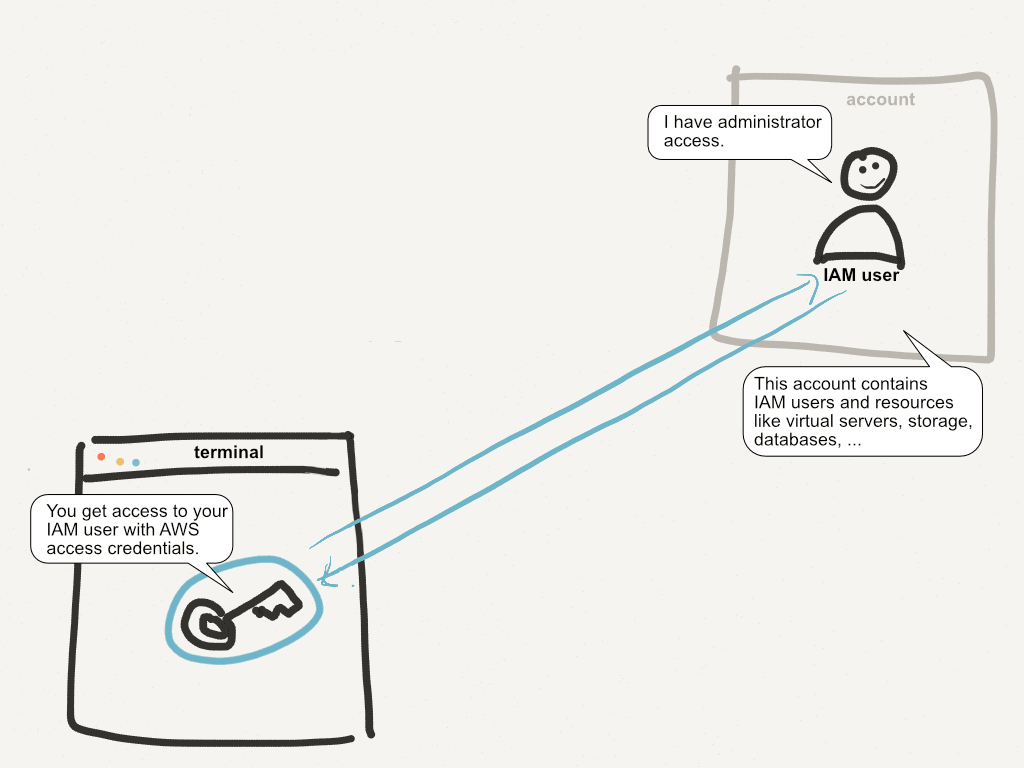
Read moreYour single AWS account is a serious risk
Your AWS account is one of the most valuable things you own if you run a business on AWS. If you only own a single AWS account, you’re facing a serious security risk! The post will show you why this a problem and how you can solve it. This post receive...
Read more