DNSSEC with Route 53: Protecting the core of the Internet
The Internet relies on DNS. This makes it all the more important to do everything possible to protect the global DNS infrastructure from attacks. Andreas explains how DNSSEC protects from DNS spoofing. During the demo you will learn how to enable DNSSEC for your domains by using Route 53.

What you will learn by watching the video and following the demo?
- Protect from DNS spoofing!
- What is DNSSEC?
- How to enable DNSSEC with Route 53?
- Pros and Cons of DNSSEC
Enjoy the video!
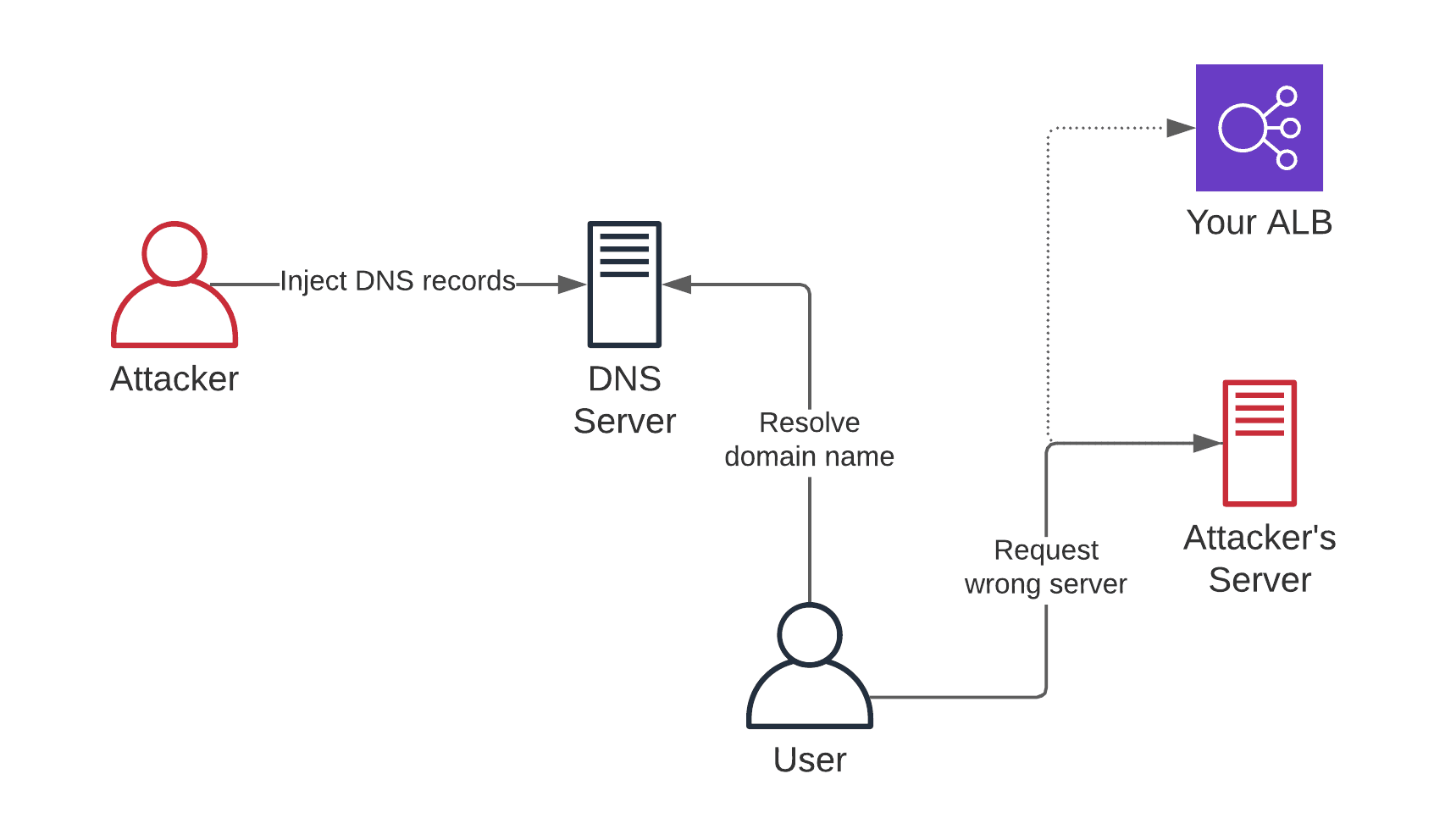
Why is DNSSEC important? Because, DNSSEC protects from the following attach, called DNS spoofing.
- Attacker injects DNS records into DNS server/resolver.
- User resolves domain name, DNS server responds with “wrong” IP address.
- User sends requests to “wrong” server.
- Attacker steals password, reads sensitive information, …
The CloudFormation templates used in the video are available at https://github.com/widdix/aws-cf-templates
I’ve used the following commands to deploy DNSSEC to us-east-1. Make sure to modify the stack names and parameters before using the commands.
aws cloudformation deploy --stack-name cloudonautio-key --template-file security/kms-key.yaml --parameter-overrides Service=dnssec-route53 KeySpec=ECC_NIST_P256 KeyUsage=SIGN_VERIFY |
When it comes to DNS, I’m using the book DNS and BIND to learn about the technical details.
A few links discussing DNSSEC:
Further reading
- Article Does your VPC endpoint allow access to half of the Internet?
- Article A Deep Dive into AWS CloudTrail
- Article AWS needs a bug bounty program
- Tag security
- Tag route53
