#security | Cloud Security (2)
All about the shared responsibility model in the cloud. Includes topics like networking (VPC), authentication and authorization (IAM), and more.
Terraform, can you keep a secret?
Did you know that Terraform state can - and most likely does - contain sensitive data? A few examples of sensitive information stored in the Terraform state: Initial password for an RDS instance. Unencrypted value fetched from SSM parameter (SecureStri...
Read moreAWS Account Structure: Think twice before using AWS Organizations
What is an AWS account? I like to use the following two ways to describe the concept of an AWS account: a tenant in Amazon’s multi-tenant cloud or a virtual data center. When running multiple workloads and environments using numerous AWS accounts is the...
Read moreShow your Tool: Parliament
In this series, we present AWS tooling from the community for the community. We talk directly with the tool makers. Who are they? What problem does the tool solve? And what motivates them to contribute to open-source AWS tooling. This time, we talk wit...
Read moreHow to secure your DevOps tools with ALB authentication?
Are you hosting any DevOps tools like GitLab, Jenkins, Kibana, Grafana, or phpMyAdmin yourself? On the one hand, it is convenient to provide access to those tools via the Internet. On the other hand, those tools add high-risk attack vectors to your infr...
Read moreHow to avoid S3 data leaks?
Not a week goes by without a frightening announcement that an organization has leaked confidential data from Amazon S3 accidentally. Most often, the root cause of a security breach is a misconfiguration of S3 access control. Do you prefer listening to...
Read moreEC2 Instance Connect is an insecure default!
Two months before, Michael wrote about why AWS SSM is a trojan horse. Shortly after that, AWS released EC2 Instance Connect, which is even worse. If you use Amazon Linux 2 or Ubuntu, the chances are high that everyone in your AWS account can SSH into ev...
Read moreAWS CloudTrail: your audit log is incomplete
Recently, I was investigating the size of a security breach caused by leaked AWS credentials. The first place to go in such a scenario is the audit log recorded by CloudTrail. When configured correctly, CloudTrail captures the requests to the AWS API an...
Read moreAWS SSM is a trojan horse: fix it now!
Recently, I held a security workshop together with a team of engineers. At some point, the team demonstrated how they use AWS Systems Manager (SSM) to run commands on a machine. What the team didn’t know: they enabled a backdoor that allows everyone wit...
Read moreMore than 25 SSL certificates with ECS
Both the Application Load Balancer (ALB) and the Network Load Balancer (NLB) provide TLS/HTTPS listeners allowing you to encrypt the data in transit from the clients to your cloud infrastructure. Together, with the Amazon Certificate Manager (ACM) ...
Read moreGoodbye SSH, use AWS Session Manager instead
SSH is great. But the AWS Session Manager - whose full name is AWS Systems Manager Session Manager - matches the needs for interacting with your EC2 instances even better. BenefitsYou should think about replacing SSH with the AWS Session Manager becaus...
Read moreThree simple rules to avoid data leaking from S3
Reviewing AWS accounts with a focus on security is part of my day-to-day job. My most common finding: unwanted public read or write access to S3 buckets. Why is that? Because there are three different ways to define who can access your S3 buckets: IAM p...
Read moreEncrypting sensitive data stored on S3
S3 comes with a bunch of features to encrypt your data at rest. Data at rest means inactive data stored physically on disk. Before we dive into encrypting data at rest, I want to highlight that there is also data in use and data in transit. If the data...
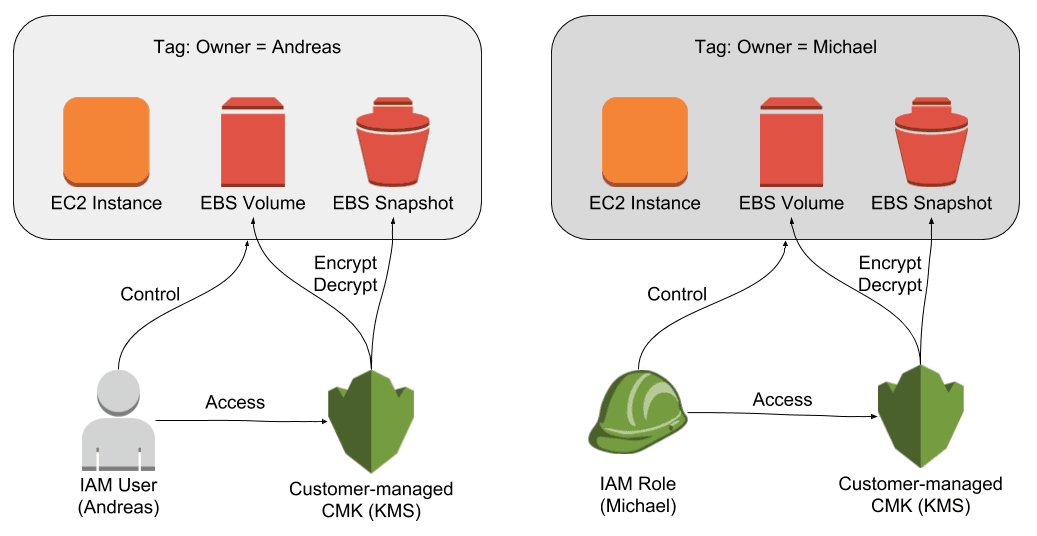
Read moreRestricting Access to EC2 Instances Based on Tags
The principle of least privilege is key when it comes to securing your infrastructure on AWS. For example, an engineer should only be able to control EC2 instances that are in scope for her day-to-day work. But how do you make sure an engineer is only a...
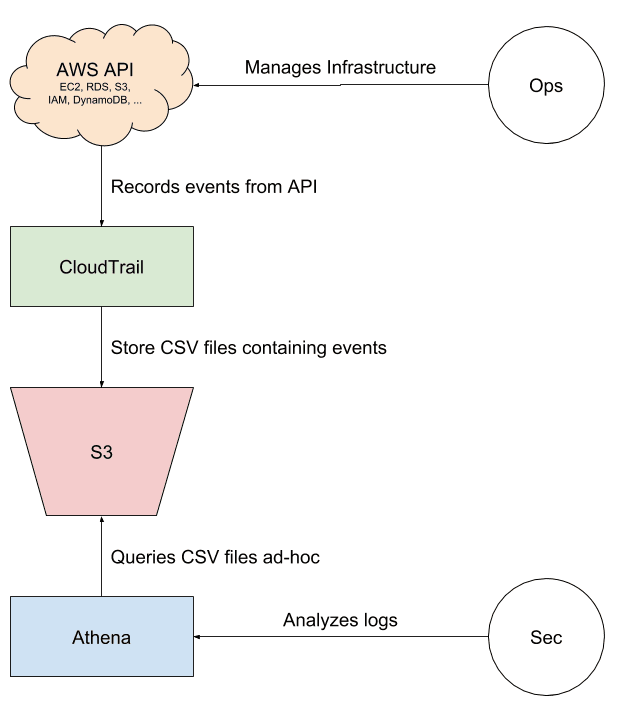
Read moreAnalyzing CloudTrail with Athena
Which IAM users have been active within your AWS account within the last 30 days? Are all of the 999 IAM roles still in use, or can you remove some of them to clean up your infrastructure? Is it safe to remove the action s3:GetObject from the IAM policy...
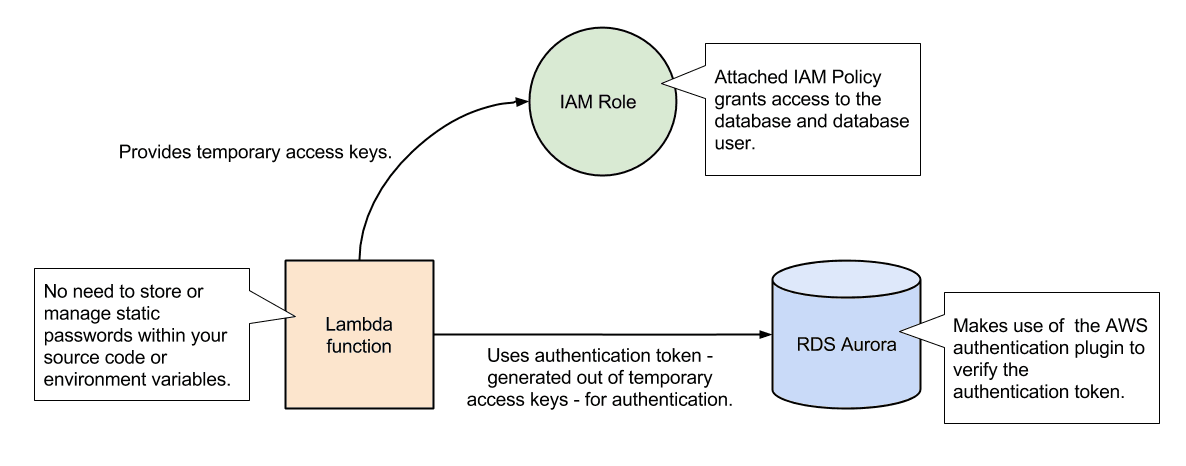
Read morePasswordless database authentication for AWS Lambda
Does your serverless application need to access an RDS database? Where do you store the username and the password required to authenticate with the database? Storing the password in plain text within your source code should not be an option. Same is tru...
Read moreAWS Security Primer
I was preparing some AWS Security related training. Soon, I realized that this topic is too huge to fit into my brain. So I structured my thoughts in a mind map1. Within a couple of minutes2 I came up with this: What is your first reaction? Mine was pr...
Read moreBeyond the default: a Multi-VPC architecture
I created my first AWS account on December 23, 2012. The one thing that surprised me most was the possibility to define private networks with Virtual Private Cloud (VPC). As this allowed me creating isolated areas, a fundamental prerequisite for buildin...
Read moreImprove Security (Groups) using VPC Flow Logs & AWS Config
As mentioned in the previous post Your AWS Account is a mess? Learn how to fix it!, most AWS accounts are a mess. This can be a serious risk, especially for security-related resources like Security Groups. In this post, we will describe a technique to m...
Read moreComplete AWS IAM Reference
Writing IAM policies is hard. Following the principle of least privilege is even harder. To write a secure IAM policy you need to know: What actions are needed? Are resource-level permissions supported and on what levels? Are conditions supported to re...
Read moreYour AWS Account is a mess? Learn how to fix it!
Have you no wildcard ec2:* in your IAM policies? Your Security Group rules are as strict as possible? Your S3 Bucket Access Policies only contain rules you know? You know about every single resource that runs in your account? If so, stop reading and ple...
Read more